Threat Protection
Automatically detect and stop known and unknown API attacks, business logic abuse attacks, as well as API abuse, fraud, and sensitive data exfiltration.

Threat Protection for the Modern Enterprise
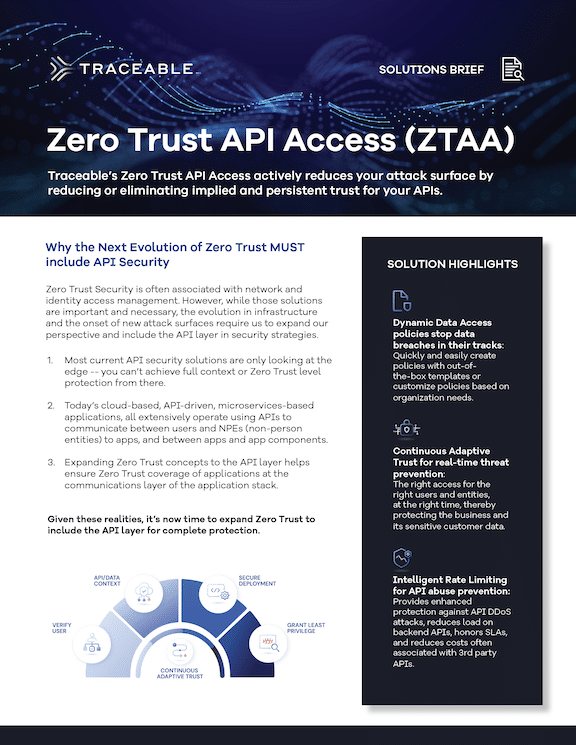
Eliminate Persistent Trust for APIs
Actively reduce attack surface by eliminating persistent trust for APIs.
Eliminate API Abuse and Fraud
Traceable provides real-time detection and protection against known and unknown API attacks and abuse.
Detect and Block API Attacks
Automatically detect and block both known and unknown API vulnerabilities, including the OWASP Web and API Top 10, business logic abuse attacks, and zero days.
Stop Sensitive Data Exfiltration
Immediately detect where hackers gain access to sensitive data by exploiting software bugs or CVEs. Understand the flow of transactions through your application, from edge to data store and back, to quickly respond and shut down the attempted theft.
DIGITAL FRAUD PREVENTION
Zero Trust API Access for Advanced Data Protection
Zero Trust API Access actively reduces your attack surface by minimizing or eliminating implied and persistent trust for APIs
Download Solutions BriefRobust Capabilities for Advanced Data Protection

Sophisticated Anomaly Detection
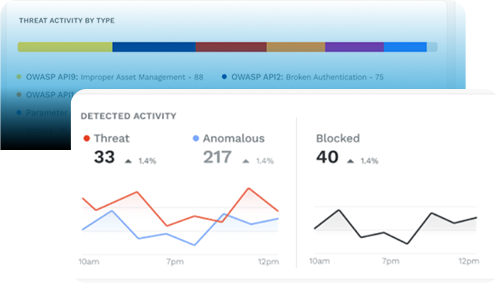
Traceable monitors how your API endpoints are communicating and how your application services are behaving. We use our machine intelligence to send ONLY valid alerts - whether its highly anomalous user behavior or an anomalous flood of incoming API calls from a foreign IP address.

Industry-leading Machine Learning Models
With a series of sophisticated algorithms, Traceable establishes a baseline of normal API behavior, app services, and data. With high accuracy, if there is an event or behavior that is sufficiently malicious based on our ML models – Traceable generates a valid security alert in real-time giving your security team and the SOC the ability to take action on any threat event happening at runtime.

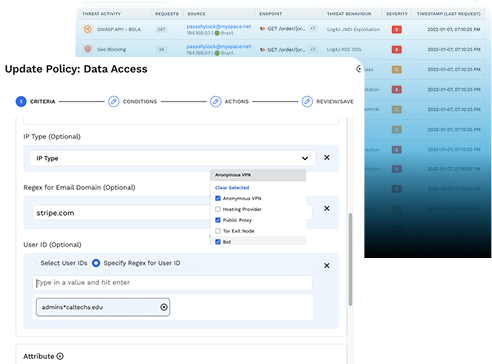
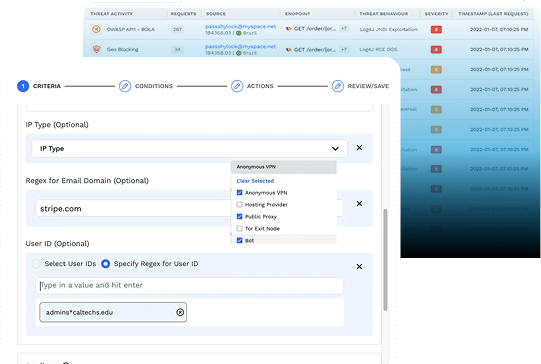
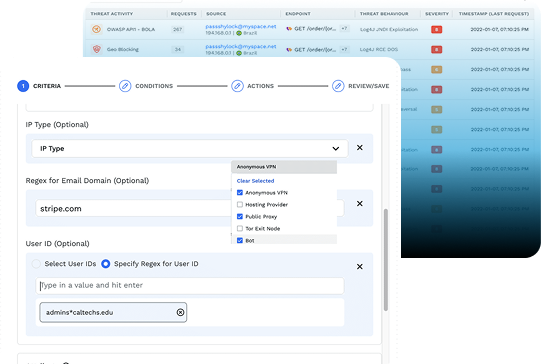
Run Policy-Based Detection and Blocking
Since Traceable is deployed at your API edge – i.e. within an API gateway, a proxy, or service mesh – we give you the ability to detect and block a variety of API and web-based attacks. You can tell Traceable to detect all remote code execution attacks, DDoS attempts, or any API object authorization bypass.

Capabilities Beyond Detection
More than just detecting, you can run Traceable in blocking mode that will prohibit any of these attacks or events across your environment. You can block threats based on threat actor, IP range, geolocation, or attack type like cross-site scripting, parameter anomalies, or recent CVEs like Log4js or Log4shell.
See why security leaders in Public Sectors love Traceable

.avif)



