API Security for Healthcare
Healthcare organizations process large amounts of sensitive patient data, and APIs allow for increased sharing of that data through the process of providing care. Traceable delivers the protection healthcare providers need to safeguard patient data and avoid costly compliance penalties.






API Attacks on Healthcare Are on the Rise
Healthcare organizations handle sensitive and personal data, such as patient medical records, billing information, and insurance information. This data is valuable to hackers and can be used for identity theft or sold on the black market.
Healthcare also have a large number of APIs that are used to exchange data with a variety of different systems and partners, such as electronic health record (EHR) systems, insurance companies, and government agencies. This can make it difficult to secure all of the APIs and ensure that they are only accessed by authorized parties.
Lastly, it's well-known that healthcare organizations are subject to strict regulatory requirements, such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States, which mandate the secure handling of patient data. Failure to comply with these regulations can result in significant fines and damage to the organization's reputation.
Overall, the combination of the sensitive nature of the data, the large number of APIs, and the regulatory requirements make API security a challenging task for healthcare organizations.
Challenges and API Risks for Healthcare Providers

Protecting Patient Data
API sprawl is a common problem for finserv and fintech organizations. They are constantly contending with a loss of control in a distributed ecosystem.
This creates unknown exposure, an unknown attack surface, and additional risk.

Legacy Systems
Sensitive data including personally identifiable information (PII), credit card numbers, SSN, and many other sensitive data types.
There are serious financial and reputational consequences in the event of a data breach.

Regulatory Compliance
Finserv and Fintech must adhere to several compliance mandates, including PCI-DSS, FFIEC, and numerous data protection laws.
Being out of compliance with any one of them can result in hefty fines and other penalties.
How Traceable Helps

API Discovery and Risk Management
Discovery all APIs in your environment and establish a baseline security posture.


Protect Sensitive Patient Data
Stop API attacks that lead to sensitive data exfiltration, API abuse and API fraud.


Maintain Compliance
Protect data and better align with PCI, PII, and HIPAA compliance standards.


Why API Security
API Security Reference Architecture for a Zero Trust World
Learn the key tenets and definitions of Zero Trust translated for APIs and much more.
Download WhitepaperHow Healthcare Providers Can Protect Patient Data with Traceable
API DISCOVERY AND GOVERNANCE
Discover and Inventory Every API
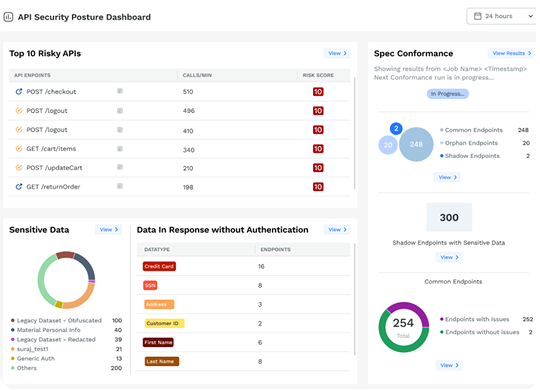
Discover and inventory all of your external API endpoints and internal APIs in a data-rich catalog for complete visibility and identification of your API estate and sprawl. Instantly see any shadow and orphaned APIs and be notified of any API changes.
For API security posture management, Traceable provides a security risk score to every APIs, which allows you to understand which of your APIs are most vulnerable to abuse. The platform does this by collecting data on runtime details such as sensitive data flows, API call maps, API usage behavior, user details, event details, threat activity levels, and more.
API THREAT PROTECTION
Instantly and Continuously Protect Sensitive Patient Data
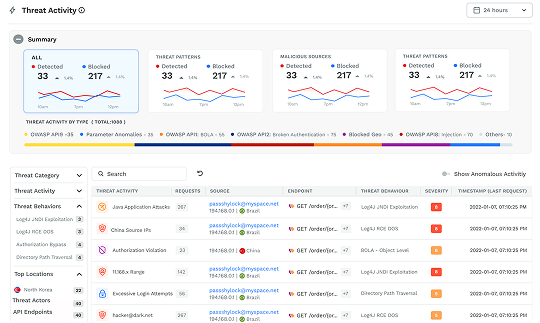
Immediately detect where hackers gain access to sensitive data by exploiting software bugs or CVEs. Understand the flow of transactions through your application, from edge to data store and back, to quickly respond and shut down the attempted theft.
More than just detecting, you can run Traceable in blocking mode that will prohibit any of these attacks or events across your environment. You can block threats based on threat actor, IP range, geolocation, or attack type like cross-site scripting, parameter anomalies, or recent CVEs like Log4js or Log4shell.
ACTIVE API SECURITY TESTING
Find and Fix API Vulnerabilities
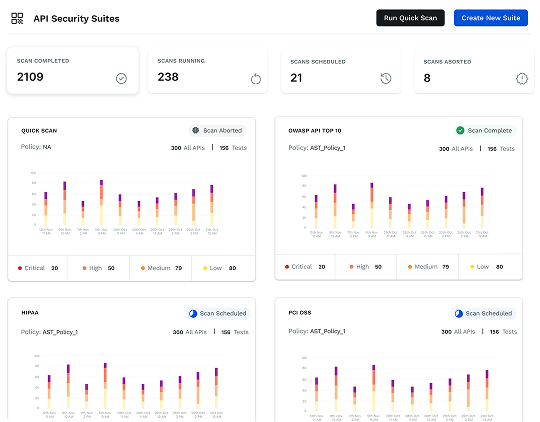
With Traceable’s API security testing, you can eliminate the risk of vulnerable APIs in pre-prod, perform rapid scans that maintain speed of innovation, and automatically obtain remediation insights for developers to better secure their APIs.
Additional API Security Capabilities Important for Healthcare Organizations
Threat Intelligence and Root Cause Analysis
It would be impossible to have effective API security without robust analytics and threat intelligence capabilities, that power root cause analysis, forensic research, and incident response.
1. API security data lake: you need to ability to collect and analyze the end-to-end path trace of all API calls and service behaviors. An API security data lake allows your SOC team, incident responders, threat hunters, as well as red teams and blue teams to conduct instant security analysis and root cause analysis.
2. Understand API traffic and user attribution: Understand API traffic history of user attributed transactions, sequences, and flows and perform post mortem reviews and analysis for any API security incidents.
3. Threat Hunting to reveal unknown API vulnerabilities: Perform threat hunting to reveal potentially unknown API vulnerabilities and visualize user behavior analytics to uncover fraud and abuse.
This level of security analytics enables SOC teams and threat hunters to optimize APIs and service behaviors to prevent the possibility of any data breach, ransomware, abuse, or data exfiltration.


Cloud Scale
An API security platform needs to be able to handle massive scale. This is especially true for large financial and retail organizations that provide tens of thousands of APIs, and need to handle billions of API calls.
This is why it's crucial to have an API security solution that is designed to process and analyze APIs, application communication, and user behavior data at cloud scale.
In addition, it should have the capability to support very large deployments consisting of thousands of API endpoints, and billion of API calls -- with flexible data collection and deployment options, including agentless or agents, depending on your needs: 1. fully out-of-band via network log analysis of AWS, GCP, and Azure Clouds, 2. Collection by instrumentation within your API gateway, proxies, or service mesh, and 3. in-app data collection through instrumentation by language-specific agents or socket filtering.
For highly regulated industries, look for a solution that can also be deployed 100% on-premise in a fully air-gapped model, without sacrificing protection, speed or scalability.
Zero Trust API Access
Enable Zero Trust API Access to Improve Enterprise and Data Security.
Today’s cloud-based, API-driven, microservices-based applications all extensively operate using APIs to communicate between users/NPE’s (non-person entities) to applications, and between applications and application components.
API Security solutions are essential to aligning Zero Trust thinking with the realities of today’s application architectures and extending the Zero Trust security model to the full application stack.
However, to date, APIs have been largely neglected by Zero Trust models. In addition, digital transformation demands and DevSecOps processes at organizations have created new gaps and vulnerabilities attackers can exploit.
As you are seeking an API security solution, look for one that is capable of enhancing your Zero Trust Security strategy. We recommend API security that can map to the NIST Zero Trust framework, as it covers reference architecture, data security, as well as compliance measures for defense in depth security.

See why security leaders in Public Sectors love Traceable

.avif)


