Evaluate Your API Security Risk with Traceable














API Sprawl
No visibility into the number of APIs, where those APIs reside, and what they are doing.
Distributed Applications
Microservice architectures make applications massively distributed, creating more risk to the organization.
Shadow APIs
Undocumented APIs create massive security and governance risks for organizations.
API Abuse
Unsanctioned access, and modifying the key functions so that APIs can be used for adversarial processes like modifying servers.
API Fraud
APIs used for fraudulent activities such as changing the price of products.
Sensitive Data Exfiltration
Using APIs to gain unsanctioned access to sensitive data, and exfiltrating it outside the organization.
Instantly know where you are exposed. Tackle API sprawl, head on. See first hand how automatic and continuous API discovery gives you comprehensive visibility into all APIs, sensitive data flows, and risk posture – even as your environment changes.
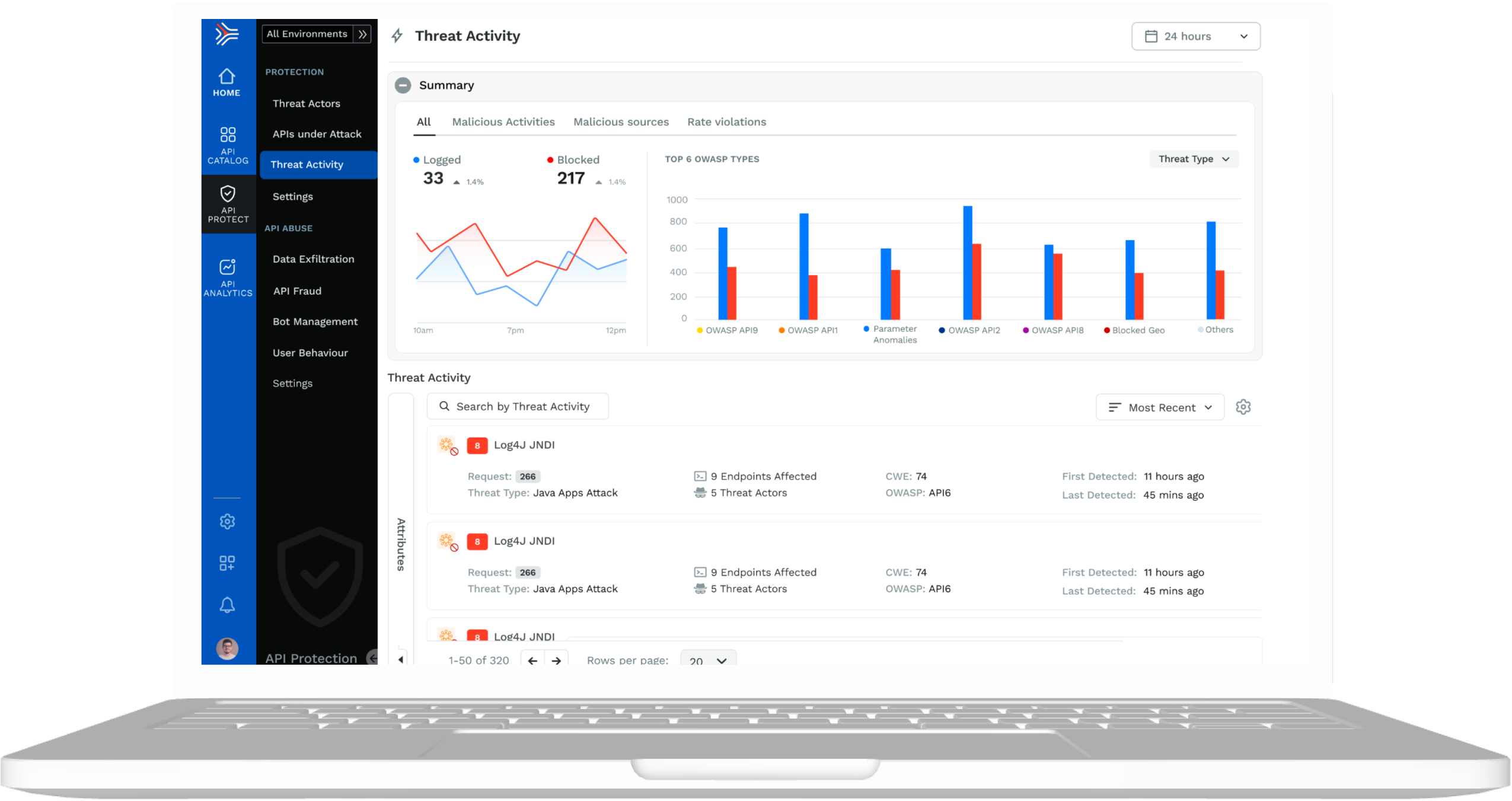
The assessment identifies all known and unknown API attacks, including internal and external API attacks, the OWASP web and API top 10, business logic attacks, API abuse, API fraud, malicious bots, and sensitive data exfiltration.
Determine how well your current security controls are working to secure your APIs. Immediately discover the signs of reconnaissance and be able to take action before attacks are successful.
Instantly know where you are exposed. Tackle API sprawl, head on. See first hand how automatic and continuous API discovery gives you comprehensive visibility into all APIs, sensitive data flows, and risk posture – even as your environment changes.
The assessment identifies all known and unknown API attacks, including internal and external API attacks, the OWASP web and API top 10, business logic attacks, API abuse, API fraud, malicious bots, and sensitive data exfiltration.
Determine how well your current security controls are working to secure your APIs. Immediately discover the signs of reconnaissance and be able to take action before attacks are successful.


API Security Summary of Findings
Detailed discovery and catalog of all APIs, including known and unknown, shadow APIs, API endpoints, sensitive data, parameters and risk scores, so you instantly know where you are at risk, and what to do about it.
Shift Left Security Evaluation
API security is especially valuable when it’s applied across the entire software development lifecycle. We’ll show you how to implement API security across build, deploy and runtime, how to actively test your APIs in pre-prod, and how to provide developers with remediation insights to further harden your APIs.
API Security best practices and recommendations
Learn how API security can become an integrated part of your data security strategy, as well as your API planning, design, and development process.
- API Discovery
- Sensitive Data Exfiltration
- Account Takeover
- Bot Mitigation
- Shift Left Security
- Incident Response
- Data Privacy
- Developer Remediation