API Data Lake for Context-Aware Security
















With this broad and deep set of data. Traceable provides the most complete security context of your APIs by building API data flows, API usage patterns (normal and abnormal), and user activity sessions that can span over extended periods. Traceable then uses this knowledge to find malicious abnormal behavior.
-
 APIs are the Universal Attack Vector What makes APIs so dangerous is that they expand the attack surface across all vectors. They present the largest attack surface we have ever encountered in the industry.
APIs are the Universal Attack Vector What makes APIs so dangerous is that they expand the attack surface across all vectors. They present the largest attack surface we have ever encountered in the industry. -
Normal vs. Abnormal Behavior Complete API security is contextually-informed, meaning, without context, you can't see and understand normal vs. abnormal behavior. Only looking at the edge, you don't have full context, therefore, it's a glorified WAF.
-
API Sprawl is Out of Control Development teams rapidly adopt, build or update internal/external 3rd party APIs to drive constant and frequent changes leading to new APIs being constantly released or updated.
Data, Identity and Risk
- Data AwareBy addressing the vulnerability of the data itself, organizations can secure data regardless of where the APIs transmit it.
- Identity AwareTraceable provides identity-aware API mapping, offering detailed visibility into API usage and enabling access control at both API and user levels.
- Risk AwareWith Traceable, you have the ability to detect and stop API threats based on the likelihood and impact that those threats might have on your business.
Complete and Verifiable Audit Details
Enables API Catalog to provide audit teams with complete and verifiable details of all API activity (malicious and non-malicious). This is especially useful where logging is found to be insufficient.
Comprehensive Security and Compliance Testing
For APIs that are rarely used, Traceable can look at historical data and replay that for vulnerability scanning. Without the historical replay capability, only those APIs that are frequently exercised can be scanned.
Enhanced Threat Detection
In addition to all the legacy attacks, Traceable can detect and protect against long-lived complex attacks starting from the reconnaissance stage. These are slow and latent attacks whose impact culminates over a period of time.
API Data Loss Prevention
Traceable detects and tracks all activity around sensitive data and data sets, including which users and APIs have accessed it, when, from what service, and if it has been exfiltrated. All this is possible to see over long periods of time for even slow leaks using the data captured in the Traceable Data Lake.
API Threat Management
Forensics such as root cause analysis of attacks and other ad-hoc security analytics is made possible by using the data lake which provides advanced query capabilities over deep historical transaction data. This also includes the threat-hunting ability to detect advanced API fraud and API abuse use cases.

to secure your APIs
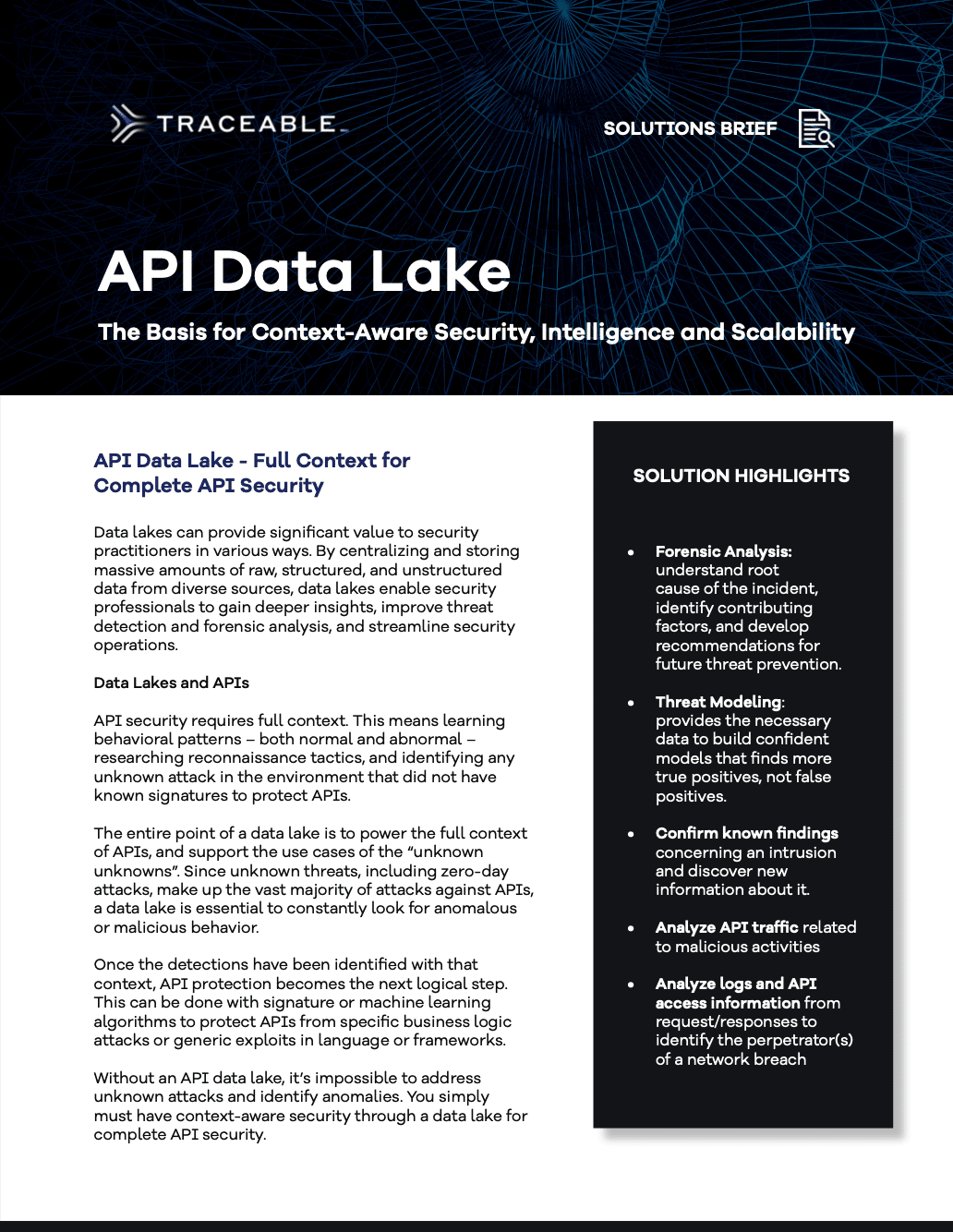
For a comprehensive API security approach, you must have the full context for each API endpoint (awareness of data, identities, and risks associated with each API endpoint).
To build this full context you need to know the following:
The API Activity
What API calls are being made at the edge? Internally? What’s the sequence of calls?
The User Activity
What does user activity look like? What are their client details (like user agent, IP, geo)? and What data is the user accessing?
The Data Flow
Where is your data flowing? When does it leave your control? Which APIs are accessing it?
The API Execution
Which parameters get used? What do requests and responses look like? What content is in the headers and bodies?
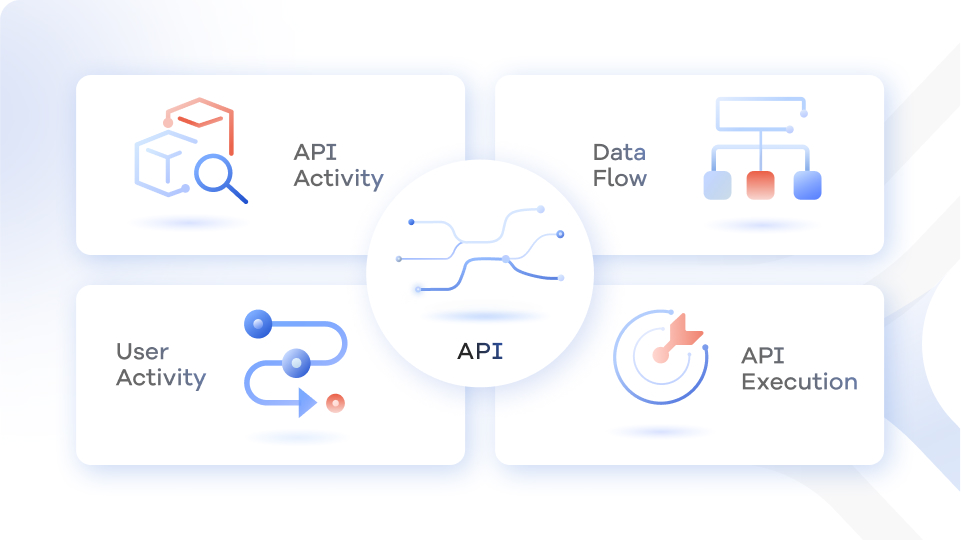
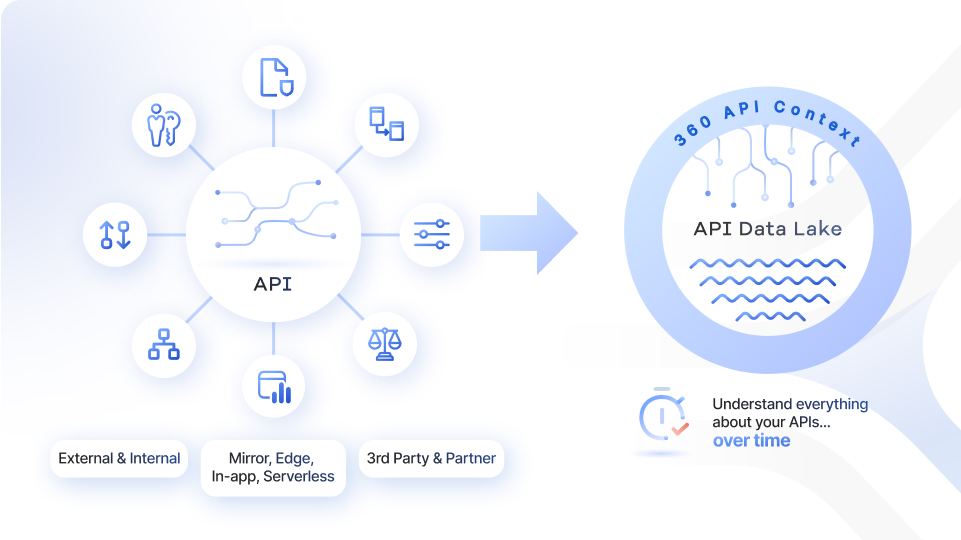
Understanding full context requires capturing and learning the details of every API call, over time. We call this “360 API context”.
The core of the Traceable platform is the API Data Lake – which enables complete API security that is context-aware, data-aware, identity-aware, and risk-aware.
Traceable captures and correlates EVERY API transaction, malicious or not, over time, because this is the only way to get a true full contextual understanding of your APIs and the attacks against them.
Traceable enables this data collection in multiple ways depending on the customer requirements – mirroring traffic, on the edge, in-app agents, and serverless. And it does this without impacting your applications.
This extra-deep understanding of every API endpoint is the foundation for all the functionalities that Traceable provides. It’s always there in the background helping to make better decisions and do better analysis.
Some particular capabilities that are more accurate, more capable, or in some cases even possible are
- Business logic attack protection
- Protection from slow and low/hidden attacks
- Protecting from zero-day attacks
- Threat hunting and forensics
- Tracking sensitive data flow and exposure
- Tracking user behavior
- Tracking application behavior
- Preventing API fraud and abuse
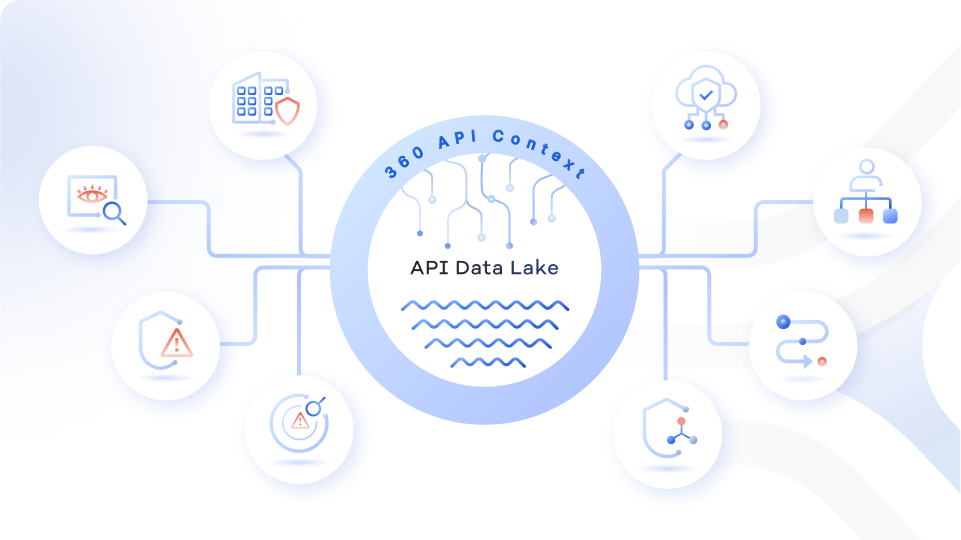
Traceable’s comprehensive API Security Platform is powered by the API Data Lake. Based on the comprehensive 360 degrees insight about EVERY API in your ecosystem, Traceable provides four key customer values:
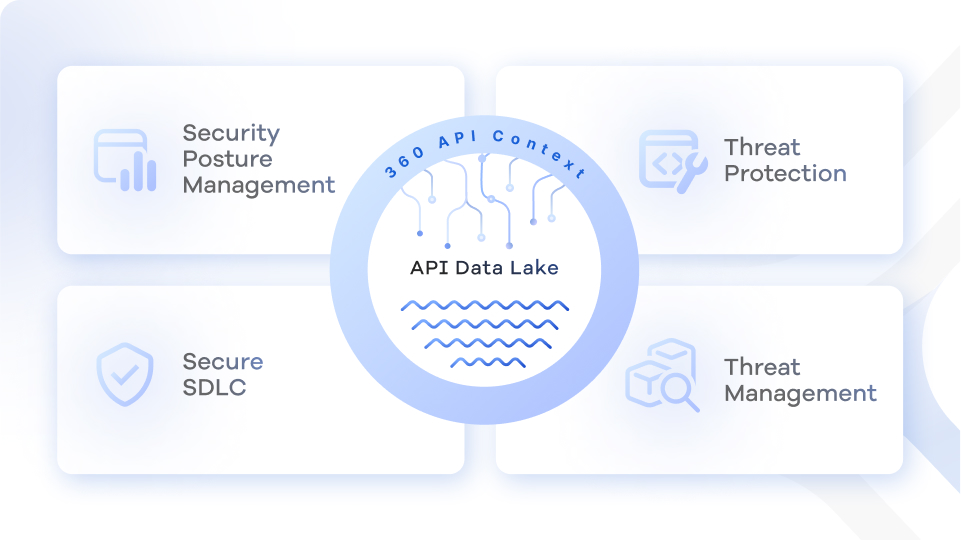
Security Posture management for your APIs
Automatic and Continuous API discovery that provides comprehensive visibility into all APIs, sensitive data flows, and risk posture – even as your environment changes.
Threat Protection for your APIs
Automatically detect and stop known and unknown API attacks, business logic abuse attacks, as well as API abuse, fraud, and sensitive data exfiltration.
Threat Management for your APIs
Explore the rich set of security and application flow analytics in the data lake that can be used by security analysts to hunt for hidden IOCs.
Secure Software Development Life Cycle for your APIs
Eliminate the risk of vulnerable APIs in pre-prod, perform rapid scans that maintain the speed of innovation, and automatically obtain remediation insights for developers to better secure their APIs.
Are Proof

to secure your APIs better