Lead from a secure foundation.
Businesses are being attacked by the most sophisticated hackers.
Today, as businesses migrate their applications to cloud-native architectures and adopt agile, DevOps practices, they are being attacked with the latest emerging tactics. Web APIs expose business logic to hackers and complex microservice environments make it easy for security vulnerabilities to sneak through the cracks. At the same time, you need to know how sensitive data moves in your apps for compliance with data privacy regulations.
Protect your business even as application architectures change, development methodologies evolve, and new threats emerge.
What’s in it for you?
Traceable brings your security and development teams together to monitor and protect your most important assets—your applications, data, and customers. It makes collaboration possible with a central dashboard, reports, and code-level threat analysis.
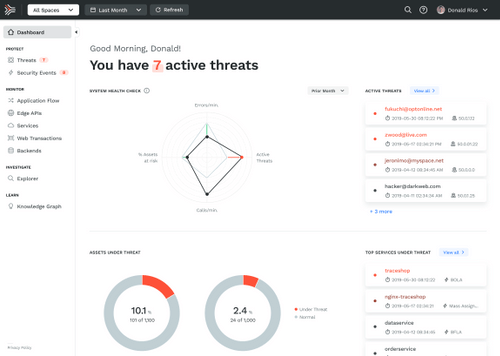
Overall application health
Dashboards surface the most urgent issues, highlight key health metrics, and report attack rates and remediation rates.
Customizable visualizations provide at-a-glance insight into service and API-level security events and load levels.
Automatic web API discovery and app topology
Real-time topology map shows API flows and interconnectivity between services (endpoints, internal, and 3rd party).
API Specifications offer more accurate specs than OpenAPI with real-time data from actual application usage.
Granular data access visibility
Data risk profiling identifies high-risk and sensitive data proactively.
Sensitive data is mapped to web APIs for transparency into the services that access sensitive data.