Stop Sensitive Data Exfiltration
Today, the vast majority of sensitive data is transmitted via API, and now more than ever, it's imperative that organizations gain visibility into their APIs and protect them from attacks.
With Traceable API security, you can stop API attacks that lead to sensitive data exfiltration, and maintain the trust of your customers, partners, and stakeholders.

APIs Are Being Used to Exfiltrate Sensitive Data
To prevent sensitive data exfiltration through APIs, organizations need to be proactive in implementing and maintaining appropriate API security measures and in monitoring and detecting potential threats. This can be challenging, but it is essential for protecting sensitive data and maintaining the trust of customers, partners, and stakeholders.
Organizations must start securing their APIs, and stop the exfiltration of data.
Top Challenges in Preventing Sensitive Data Exfiltration

Abuse and Misuse
APIs are being abused and misused in ways that result in the exfiltration of sensitive data, including DOS attacks, abuse of functionality, as well as fraudulent activities.
Lack of Visibility
API Sprawl creates a lack of visibility into APIs and the sensitive data that flows between them, making it harder to monitor and detect potential data leakage.
Unauthorized Access
Unauthorized users can perform actions or access information that they should not be able to. This can result in sensitive data exfiltration.
How Traceable Helps Stop Sensitive Data Exfiltration
Complete API Visibility
Discover and catalog all APIs in your environment - internal, external, 3rd-party, and partner, and sensitive data flows between them.


Stop API Abuse and Fraud
Protect your APIs from unauthorized or malicious use, ensuring the security and reliability of your API ecosystem.


Deep Threat Intelligence
Rich security and application flow analytics in a data lake which can be used for threat hunting and root cause analysis.

How to Prevent Sensitive Data Exfiltration with Traceable
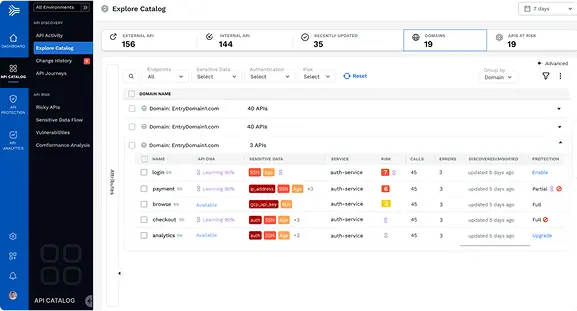
API DISCOVERY AND INVENTORY
Complete API Discovery
The first step in preventing sensitive data exfiltration, is to gain complete visibility into your API sprawl.
Traceable automatically discovers all of your APIs in a data-rich catalog for a complete always up-to date inventory of your API ecosystem. This includes HTTP, RESTful, GraphQL, SOAP, XML-RPC, JSON-RPC, and gRPC.
This ultimately addresses lack of visibility, also identifying any shadow and orphaned APIs, and notifies of any real-time API changes. Traceable maps your app topologies, any data accessed by any APIs, and sensitive data flows, including connectivity between edge APIs, internal services, and data stores.

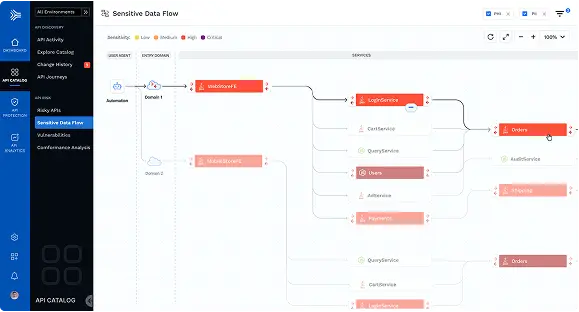
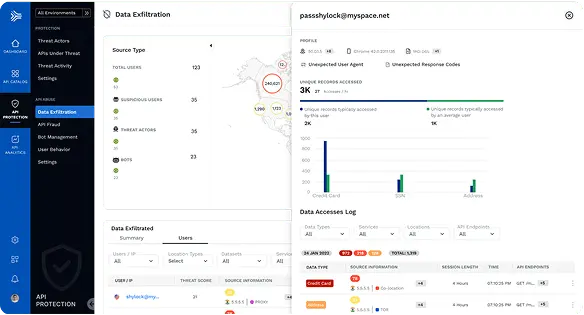
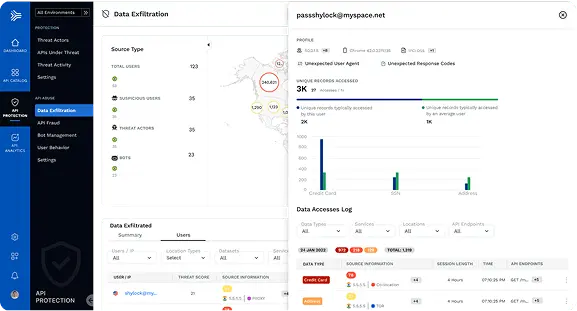
DETECT SENSITIVE DATA
Visual Depictions of Sensitive Data Flows
An important aspect to API Discovery is being able to see exactly where sensitive data resides and where it traverses across multiple points.
API Catalog maps your app topologies and data flows, including connectivity between edge APIs, internal services, and data stores.

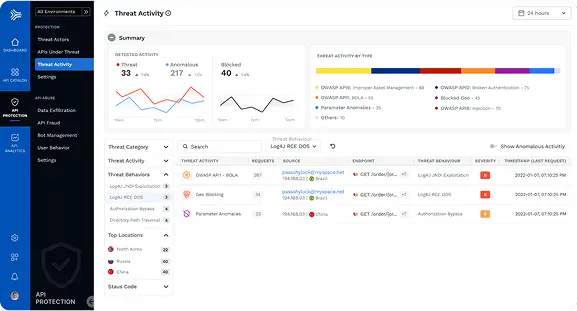
STOP API ATTACKS
Unparalleled API Threat Protection
Automatically detect and stop known and unknown API attacks, business logic abuse attacks, as well as API abuse, fraud, and sensitive data exfiltration.
1. Detect anomalies, exfiltration, attacks
2. Runtime exploit prevention
3. Defend against attacks- OWASP Web Top 10, OWASP API Top 10, and many others.
4. User and threat actor tracking
5. Business Logic Abuse Protection
6. Stop data exfiltration, fraudulent activities, and bot mitigation
7. Create and track incidents and other security issues

STOP DATA LOSS
Shut Down Data Theft
Immediately detect where hackers gain access to sensitive data by exploiting software bugs or CVEs. Understand the flow of transactions through your application, from edge to data store and back, to quickly respond and shut down the attempted theft.
We use our machine intelligence to send ONLY valid alerts – whether its highly anomalous user behavior or an anomalous flood of incoming API calls from a foreign IP address.

See how Traceable (and it's API Data Lake) helps you to secure your APIs
See our API Security Platform in action
Request a DemoAdditional Capabilities for Complete API Threat Protection

Data Collection and Deployment Built for Massive Scale
1. fully out-of-band via network log analysis of AWS, GCP, and Azure Clouds,
2. Collection by instrumentation within your API gateway, proxies, or service mesh, and
3. in-app data collection through instrumentation by language-specific agents or socket filtering.
For highly regulated industries, Traceable can be deployed 100% on-premise in a fully air-gapped model, without sacrificing protection, speed or scalability.
Zero Trust API Access
Today’s cloud-based, API-driven, microservices-based applications all extensively operate using APIs to communicate between users/NPE’s (non-person entities) to applications, and between applications and application components.
API Security solutions are essential to aligning Zero Trust thinking with the realities of today’s application architectures and extending the Zero Trust security model to the full application stack.
However, to date, APIs have been largely neglected by Zero Trust models. In addition, digital transformation demands and DevSecOps processes at organizations have created new gaps and vulnerabilities attackers can exploit.
Traceable's API security platform builds on your Zero Trust Security strategy. We map to the NIST Zero Trust framework, as it covers reference architecture, data security, as well as compliance measures for defense in depth security.


API Threat Protection
Traceable offers runtime exploit protection that automatically detects and stops known and unknown API attacks, business logic abuse attacks, as well as API abuse, fraud, and sensitive data exfiltration.
Additional Details:
1. Eliminate API Abuse and Fraud: you need real-time detection and protection against known and unknown API attacks and abuse.
2. Detect and Block API Attacks: Automatically detect and block both known and unknown API vulnerabilities, including the OWASP Web and API Top 10, business logic abuse attacks, and zero days.
3. Stop Sensitive Data Exfiltration: Immediately detect where hackers gain access to sensitive data by exploiting software bugs or CVEs. Understand the flow of transactions through your application, from edge to data store and back, to quickly respond and shut down the attempted theft.
Threat Intelligence and Root Cause Analysis
Traceable provides robust analytics and threat intelligence capabilities that power root cause analysis, forensic research, and incident response.
1. API security data lake: collect and analyze the end-to-end path trace of all API calls and service behaviors. An API security data lake allows your SOC team, incident responders, threat hunters, as well as red teams and blue teams to conduct instant security analysis and root cause analysis.
2. Understand API traffic and user attribution: Understand API traffic history of user attributed transactions, sequences, and flows and perform post mortem reviews and analysis for any API security incidents.
3. Threat Hunting to reveal unknown API vulnerabilities: Perform threat hunting to reveal potentially unknown API vulnerabilities and visualize user behavior analytics to uncover fraud and abuse.
This level of security analytics enables SOC teams and threat hunters to optimize APIs and service behaviors to prevent the possibility of any data breach, ransomware, abuse, or data exfiltration.

Deploy with Confidence
Traceable values our channel partners as an extension of our team to drive the most value for our mutual customers.
With an extensive range of deployment options, you can discover and secure APIs across your entire digital enterprise.

Self-Managed
On-Prem or Cloud
Cloud
AWS, GCP. Azure or customer datacenter
Saas
Software as a Service
See why security leaders in Public Sectors love Traceable

.avif)


