How API Flaws Allowed Students to do their Laundry for Free


Many consumers are big fans of smart appliances and toys for their ease of use and integration into their smart home setups. It is very alluring to be able to pull up an app on your phone to turn on the lights or heat up your oven.APIs often power these features that consumers have come to enjoy. However, whenever you can remotely access your smart device, there is always a chance that someone else can too if the manufacturer has not implemented proper security measures. Tech-savvy consumers may also figure out how to tamper with their appliances in ways the manufacturer didn’t intend. Such tampering can result in real business loss if the security failure involves the exchange of money. One such incident has caused a wave of media coverage recently - a connected/smart laundry system created by CSC ServiceWorks could be tricked into giving free laundry cycles. Students at UC Santa Cruz discovered API flaws to bypass the need for payments and even fill their laundry account with millions of dollars.
Checking pockets for any hidden goodies (or Swagger UI docs)
When you want to probe an API for security flaws, a common first step is to try and find documentation. For public APIs, a lot of documentation is usually available and easy to find. For private or internal APIs, documentation is almost always never available publicly because the company didn’t intend for others to use the APIs. The availability of documentation can help security researchers by saving them considerable time. Instead of reverse engineering binary files or JavaScript, an Open API spec can provide everything that is needed to probe an API for weakness, and sometimes even reveal internal APIs that unlock privileged access.Swagger UI is a documentation platform designed for APIs. CSC ServiceWorks used it to document their API. They accidentally left it exposed for anyone to view (if they knew where to look). This made it easy to work with the API and removed the need to reverse engineer anything. Here is an example of an API call where all request fields are clearly documented:
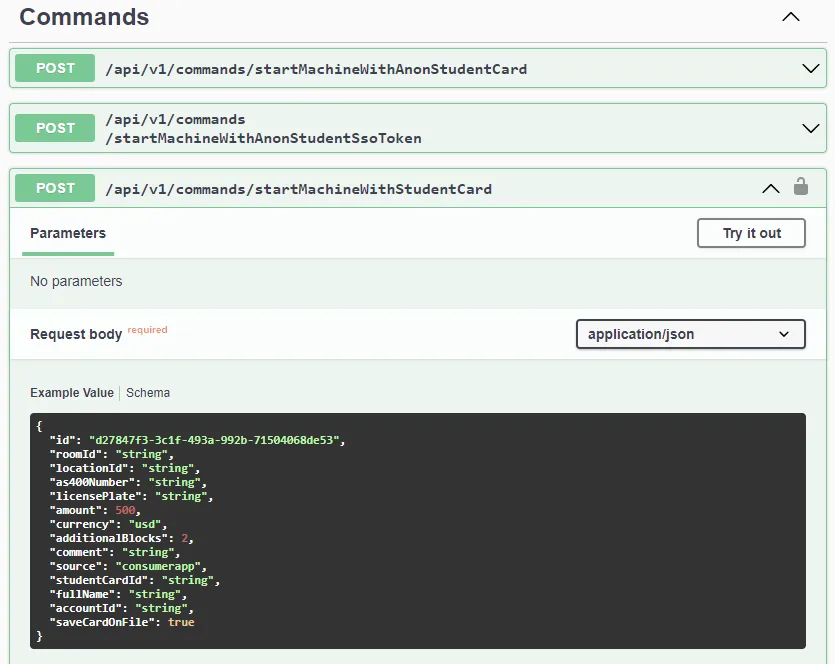
Starting a load: Exploiting the API for free cycles
With the documentation in hand, it didn’t take long to discover some interesting API requests with body parameters that shouldn’t be there. There were at least 2 critical vulnerabilities in the API that ultimately allowed to start a laundry machine for free. Both vulnerabilities are examples of Broken Object Property Level Authorization.The first vulnerability was with the startMachineWithPayment API. If you look closely, you will notice how there is an amount field:
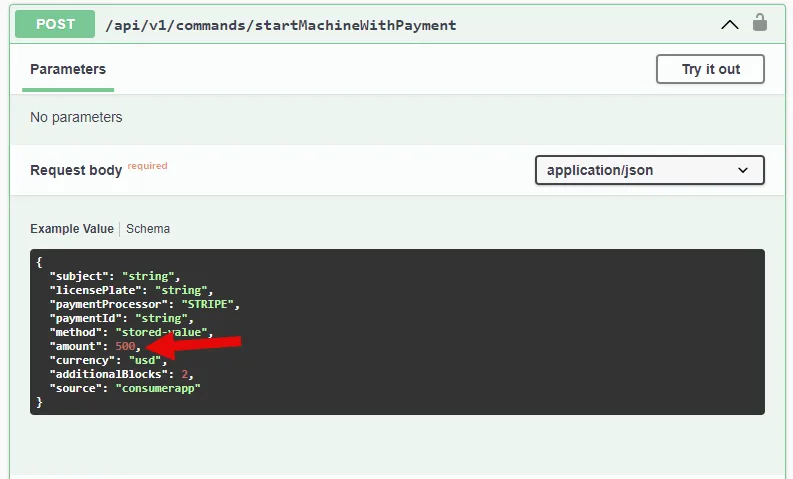
This was an important discovery because it indicated the client had control over how much they were spending. Instead of the server deducting a set amount of money from the account, it relied on the client to tell them how much to deduct. When it was set to 0, no money was deducted, but the laundry machine still started. With this vulnerability, it was unnecessary to add any funds to your account, but to get any laundry done, you would have to send this API request manually each time, which would get tedious. Sometimes you just want to start a load quickly and get back to studying (or partying). Fortunately, the second vulnerability made things even easier.The second vulnerability was with the deposit API itself. You buy laundry credit using an external payment processor, and then the CSC API to actually add the funds would be called with the amount you paid:
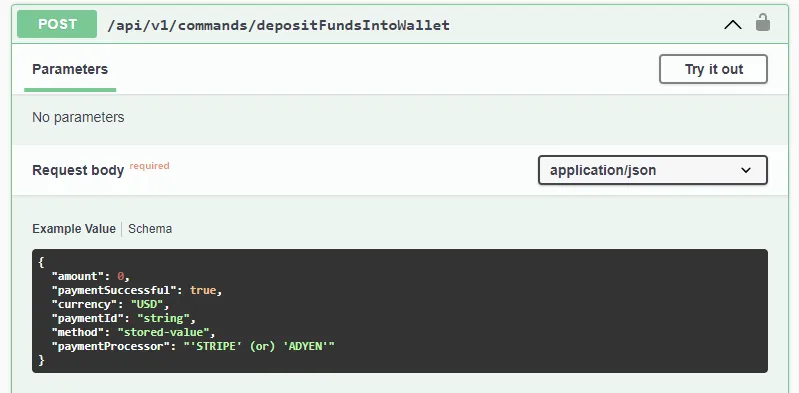
The issue was once again the API blindly accepting a client-provided amount. The actual purchase could be bypassed entirely. If you wanted a million dollars for your laundry, you would put that in the amount field and the API server would happily accept it. It didn’t actually check with the payment processor that you actually paid the amount. You would be free to do laundry for the rest of your days without having to worry about money again!
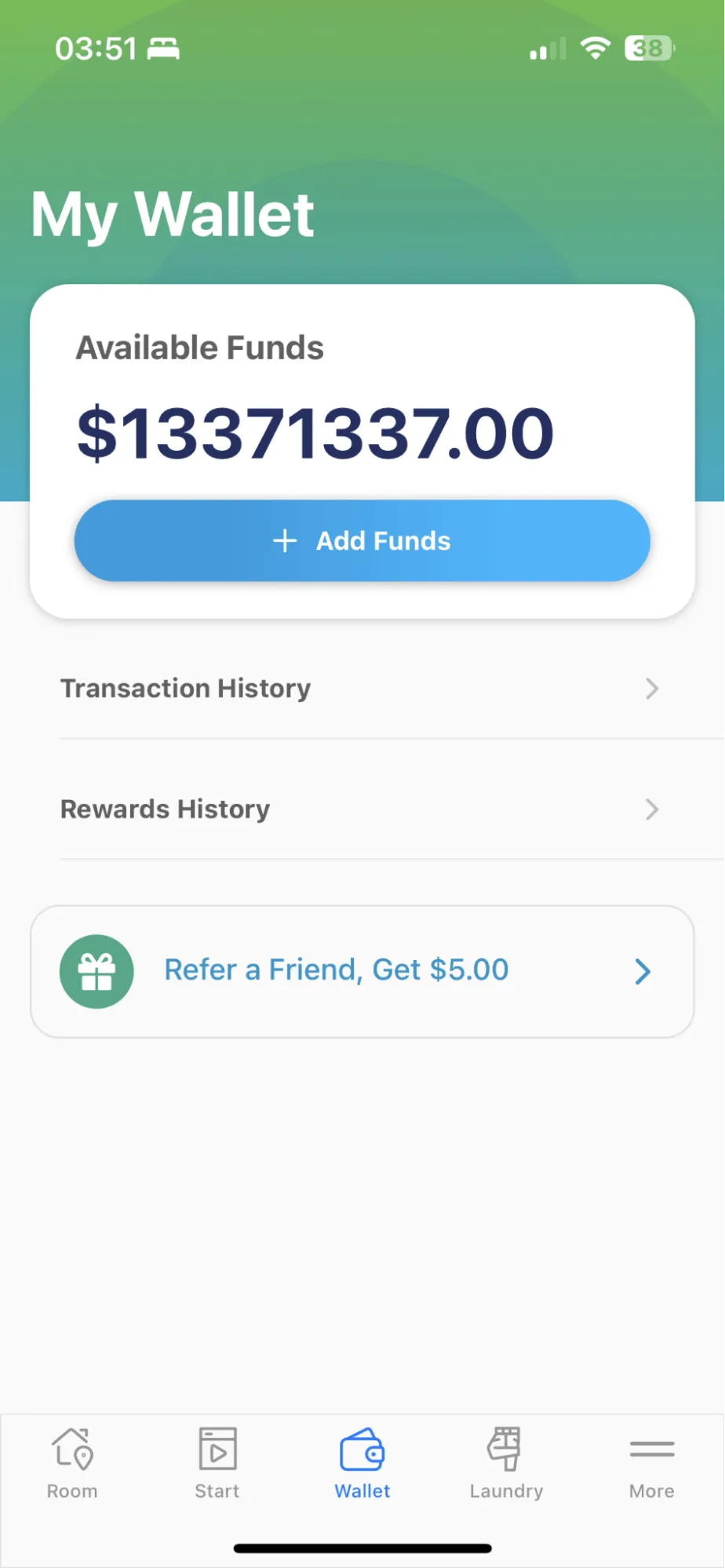
$13 million laundry credits ought to be enough for anybody, but it wouldn’t hurt to refer a friend to get a little more! Slug Security/slugsec.ucsc.edu
Previous trouble with hot water
Back in 2022 there was another eerily similar incident involving a hot water appliance: Jacuzzi SmartTubs. There was a critical API flaw that allowed any logged in user to access all the admin functions and user information. Missing access controls made this possible. The issue was eventually resolved after a similarly long disclosure and serves as another warning about the potential dangers of “smart” platforms. You should be cautious about what data you put into these platforms and how deeply you integrate them into your network. Many smart device manufacturers do not dedicate a lot of time to securing their products, and these incidents clearly show that it needs to start becoming more of a priority - especially when money is involved.
Traceable ASPEN
Traceable ASPEN provides vendor neutral and threat driven research in API security, investigating the latest breaches with world leading expertise and analysis. We believe in securing the world’s APIs with actionable insights from across the industry. We are offensively minded, defensively driven, and focused on your protection.
The Inside Trace
Subscribe for expert insights on application security.
.avif)


