Traceable API Security Platform Updates - May 2024


This past month’s releases include a major update for organizations monitoring the compliance posture of their APIs: Traceable Compliance Policies and Issues. We’ve also released span filters for fine-grained targeting of API security tests, an update to our Cloudflare WAF integration, and new detection logic for credential stuffing attacks.
Compliance Policies & Issues Dashboard
Maintaining an accurate and up to date API inventory and strong security controls around APIs are key requirements of many organizations’ security and compliance programs. Many organizations maintain and enforce their own organization-specific security policies in addition to monitoring compliance against industry or data-specific regulatory frameworks such as PCI-DSS. Traceable’s new Compliance Policies make it easier than ever to maintain and monitor the compliance posture of your APIs against specific requirements. With Compliance Policies you can:
- Easily monitor and maintain compliance with your organization’s security policies or specific regulatory frameworks like PCI-DSS
- Create fine-grained custom policies for your organization’s specific requirements
- Continuously identify endpoints that violate your organization’s policies, so you can act quickly to repair your compliance posture
- Review and triage compliance-related issues along with API security testing findings from a unified “Issues” dashboard
- Compliance policies come seeded with some recommendations from Traceable that we see most commonly in our customer’s environments. You can find those under the “Traceable Recommended Policies” section.
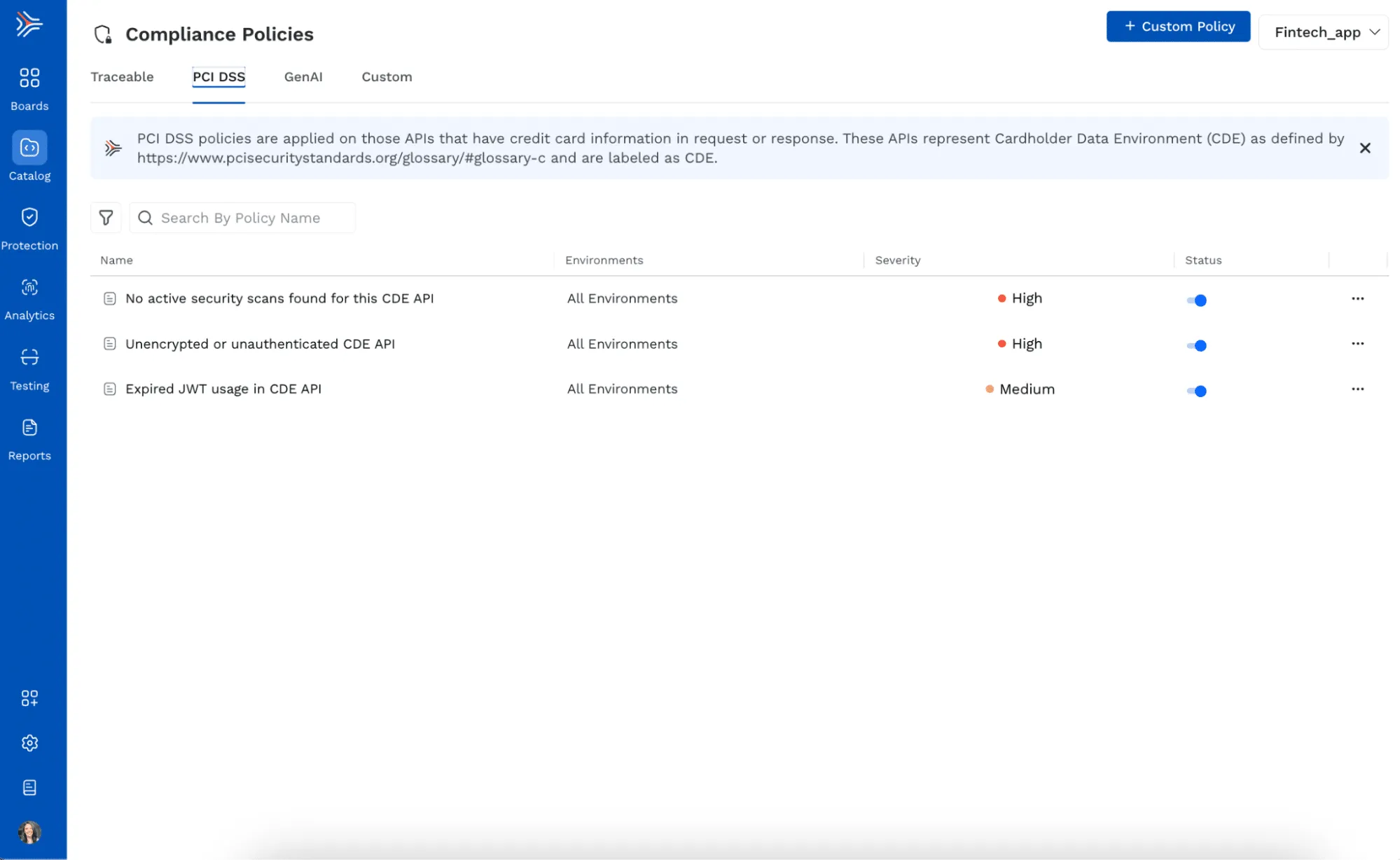
You can use Compliance Policies to identify violations apart from the standard vulnerabilities that Traceable already identifies. We have included Traceable-recommended Compliance Policies and PCI-DSS Compliance Policies out of the box. PCI-DSS applies to any organization processing payment card information. Our PCI-DSS policies automatically identify API endpoints that expose credit card data and haven’t been scanned for vulnerabilities in the last 30 days, lack encryption or authentication, or contain specific vulnerabilities.
You can also create fine-grained Custom Policies to support and track your organization’s specific compliance requirements. Custom Policies can be configured to identify violations based on various attributes, such as the environment the API is present in, its vulnerability type, and sensitive data in requests and responses.
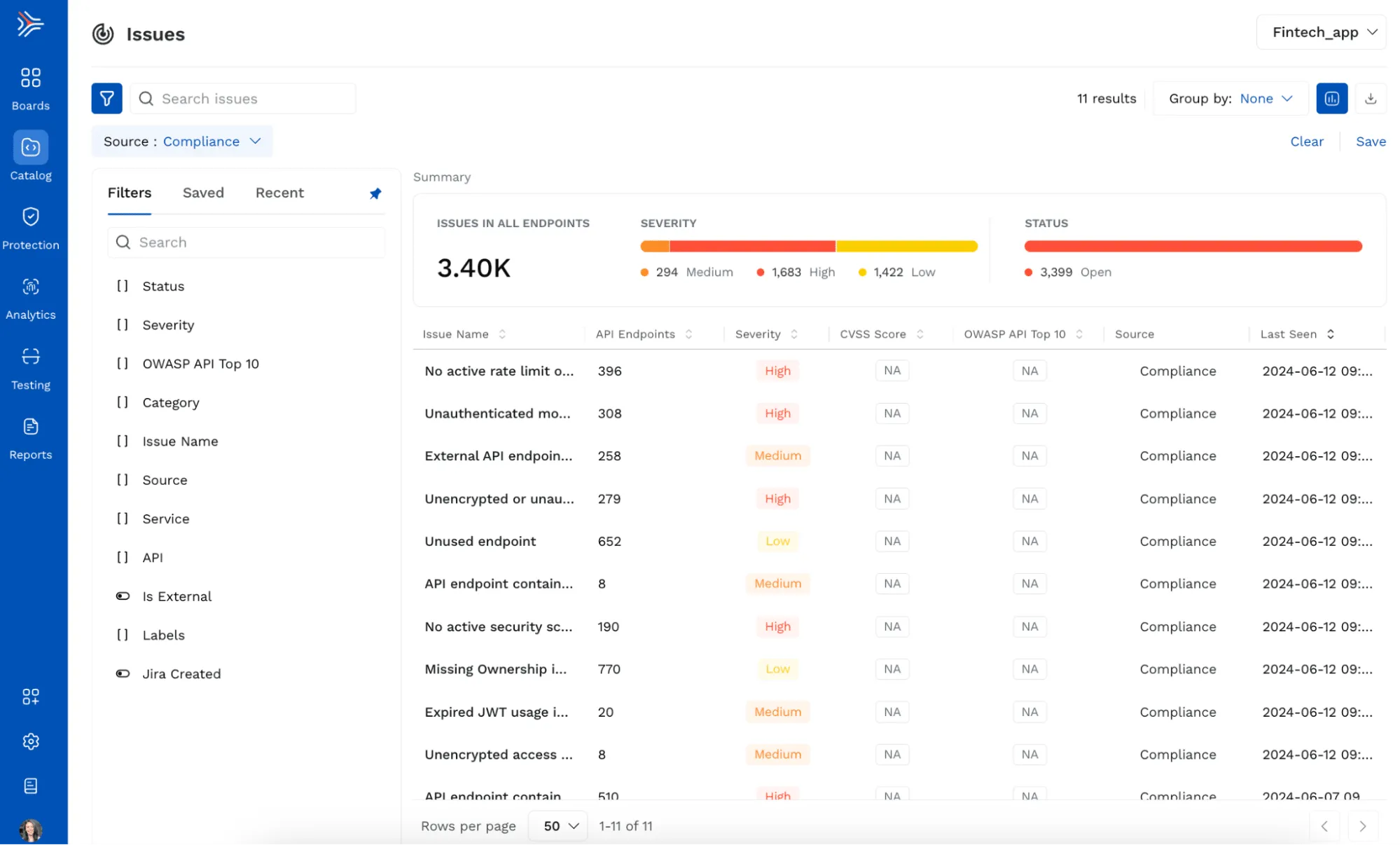
Violations identified via Compliance Policies will be surfaced in the “Issues” dashboard (formerly Vulnerabilities) which also includes findings from API security testing. You can filter by Source and select Compliance to view and triage all compliance issues.
Fine-Grained Filters for Targeted API Security Testing
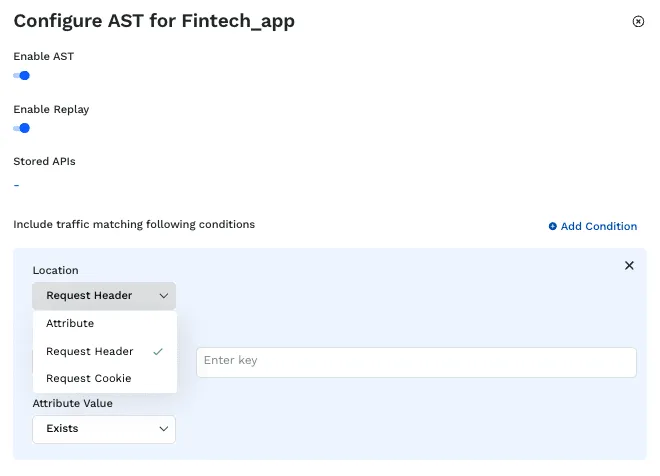
We have added new filters within API Security Testing to enable you to create and run targeted tests on a subset of API traffic. This enables you to run fine-grained tests more quickly and efficiently. Filtering is now available as a configuration option within individual Test Suites, or in your Environment Configuration when replay is enabled. Filters can be configured to test only a subset of the traffic based on key value pairs for attributes, request headers, and request cookies.
Enhancements to Credential Stuffing and Volumetric Attack Detection
Credential stuffing is an attack technique in which hackers leverage a list of credentials, usually obtained from a data breach or purchased on the dark web, and attempt to login to an unrelated service. This technique can be successful because many people still repeat the same usernames and passwords across services, allowing an attacker to take the stolen login from a compromised service and successfully login to a victim service. These attacks typically leverage automation from bots to test a large volume of credentials against the login flow. More sophisticated attackers may “drip” login attempts over time to evade bot detection.
Traceable has made enhancements to credential stuffing detections. These detections leverage behavioral baselines for login attempts per API endpoint involved in the signup/registration and login process. By tracking behavior across successful and failed login attempts, and using a combination of request parameters, status codes, and volumetric thresholds, we identify and block credential stuffing attacks.
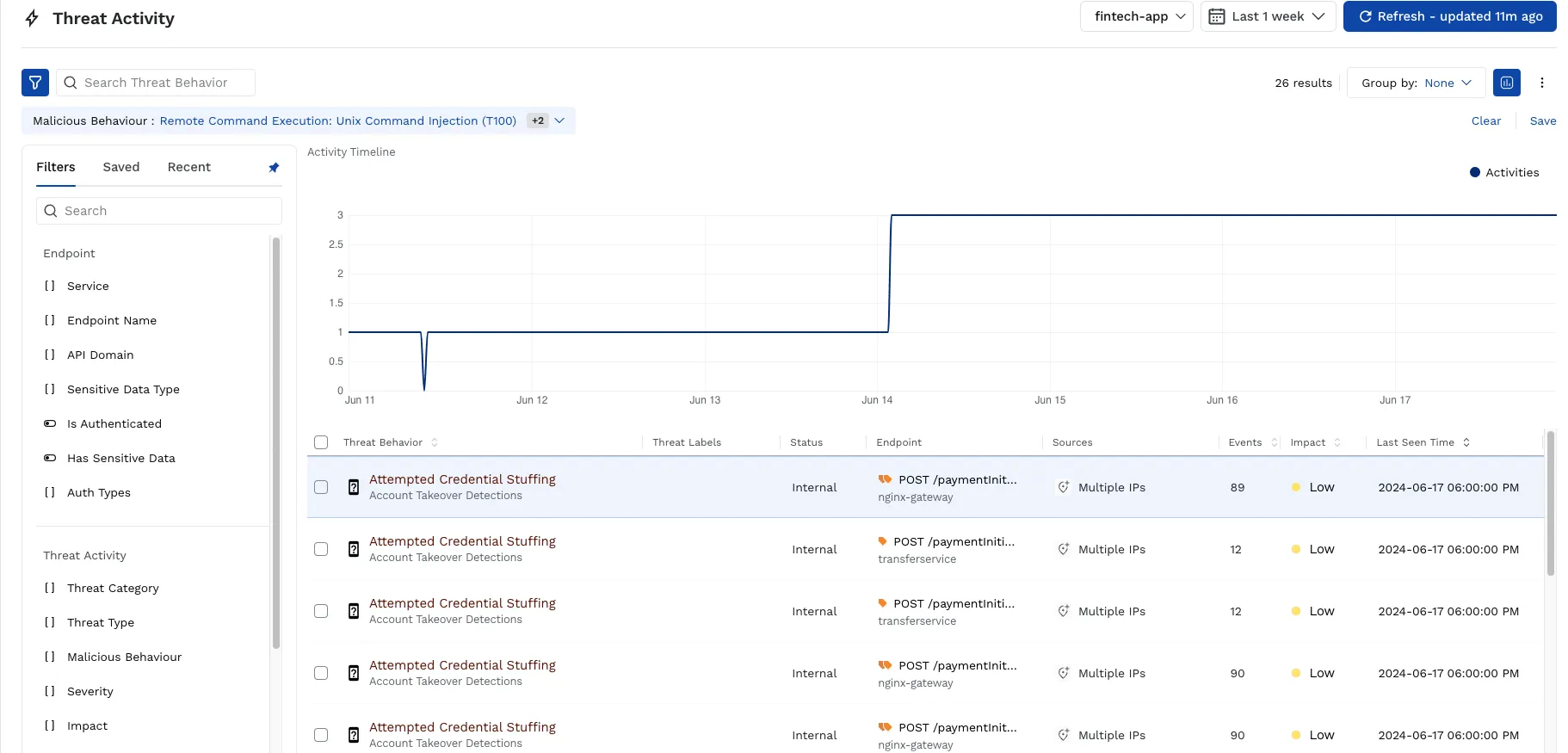
We have also made improvements to volumetric attack detection. We detect spikes in API call counts out of the box by creating behavioral baselines for normal call volumes so that any time there is unusual activity it can be detected right away.
In both detections the sources of traffic involved are grouped based on common characteristics like IP ASN and Organization so that reliance on IP addresses alone is reduced as distributed volumetric attacks typically involve thousands of individual IP addresses which can hide behind proxies, vpns etc.
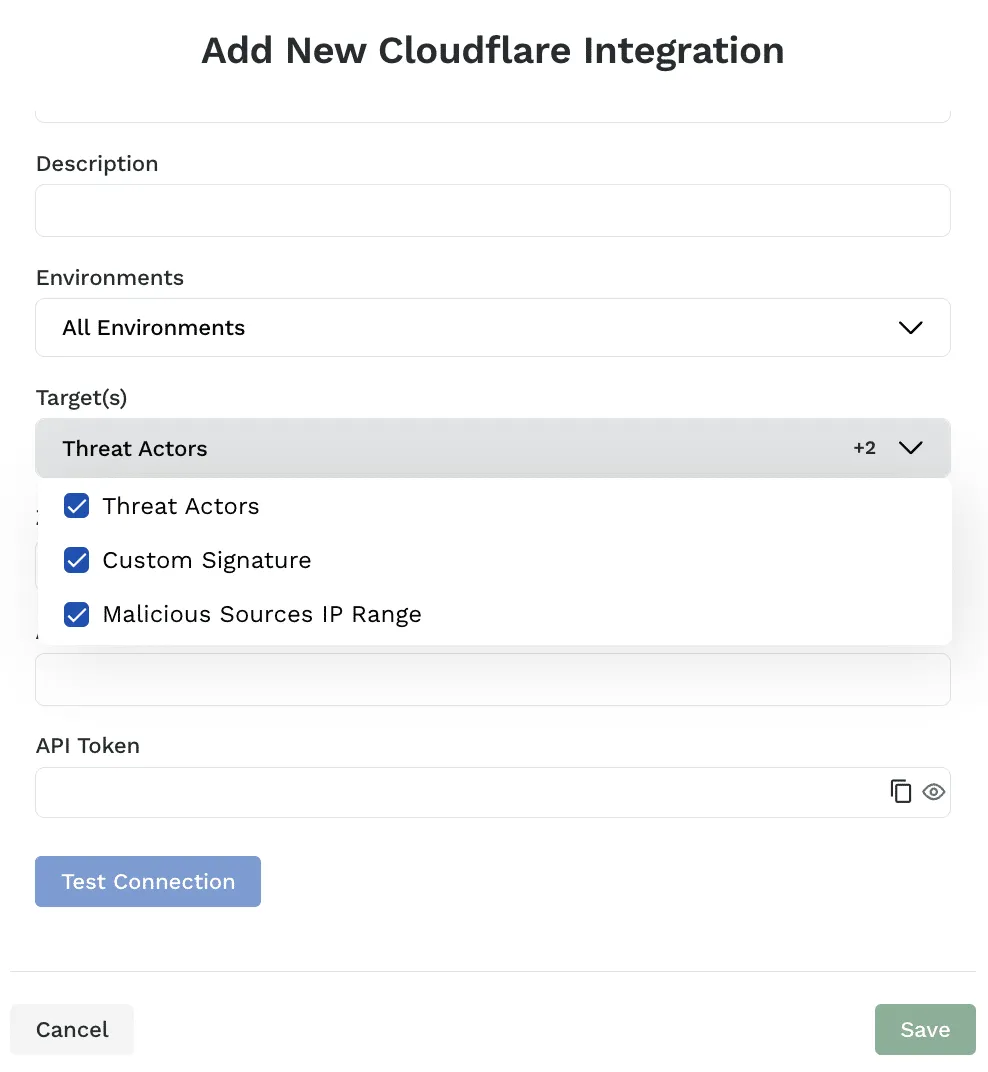
Custom Signature Support for Cloudflare WAF Integration
We have updated our Cloudflare WAF integration to include support for custom signatures. Custom signatures that you create in Traceable can now be pushed to Cloudflare for out-of-band blocking via the Cloudflare WAF in addition to the current IP based blocking.
About Traceable
Traceable is the industry’s leading API Security company helping organizations achieve API protection in a cloud-first, API-driven world. Traceable is the only contextually-informed solution that powers complete API security – API discovery and posture management, API security testing, attack detection and threat hunting, and attack protection anywhere your APIs live. Traceable enables organizations to minimize risk and maximize the value that APIs bring to their customers. To learn more about how API security can help your business, visit https://www.traceable.ai/.
The Inside Trace
Subscribe for expert insights on application security.
.avif)



