Drop-in API security for your Kong deployments
Stronger API Security with Traceable AI for Kong
The Kong API Gateway is a great centralized solution that enables organizations to manage the entire lifecycle of their APIs. For security, Kong offers capabilities such as access control, rate limiting, and authentication to help manage the basic protection of your APIs.
Beyond basic threats, APIs now face increasingly sophisticated attacks. Protecting against these requires a dedicated security solution that understands application context and user behavior.
With the Traceable AI plugin for Kong, organizations can deploy advanced API security directly on their gateway, safeguarding mission-critical applications. Powered by distributed tracing, Traceable AI maps microservices end-to-end, learns normal behavior, and detects anomalies in real time—alerting or blocking as needed to ensure resilience.
Key Benefits

API Discovery
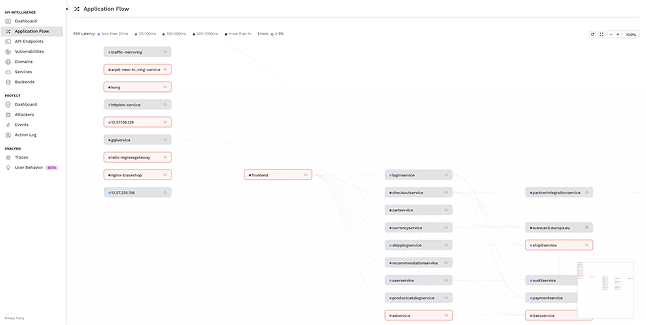
Traceable AI monitors stateless API traffic to reconstruct the full API DNA including the name, parent service, headers, parameters and payloads to provide full visibility and change management for external and internal APIs.

API Intelligence & Risk Monitoring
Per endpoint risk scores and threat indexes help prioritize focus. Risk scores are continuously calculated based on the likelihood and possible impact of an attack. Threat indexes show the current level of threat activity.
Prevent Sensitive Data Exposure
Pinpoint transactions where sensitive data is exposed. Identify API endpoints that handle sensitive data. See meta-data details of all data used by all endpoints. Identify external (north-south) facing APIs. Identify APIs endpoints without authentication.
OWASP API TOP 10 - API Protection
Ensure API protection, prevent the exploitation of API vulnerabilities that can lead to sensitive data loss. Protect against BOLA, Mass Assignment and other business logic vulnerabilities.

OWASP TOP 10 - Web Protection
Traceable AI analyzes web traffic as it passes through your application, blocking cyber-attacks before they can get your sensitive data. Protect against web application attacks such as SQL injections, Cross-site Scripting (XSS) and XML External Entities (XXE).

Security Analytics
Extract critical security insights from all transactions captured in a data-lake. Powered by machine learning, Traceable AI can surface potential threats and ensure you’re ahead of your attackers.

Resolve Threats Faster
Visualize security events as kill chains as executed by cybercriminals, helping to streamline threat analysis, forensics, and remediation.
Triage Attacks Faster
Decrease analysis time by reviewing aggregated security events without having to parse through hundreds of log files across microservices.

Perform Deep Forensics
Drill down into system behavior and identify the errors, users, URL, possible security events and relevant parameters needed to address the risk.
See why security leaders in Public Sectors love Traceable

.avif)