Holiday Hacks: Unraveling API Exploits Fueling Digital Fraud


With the holiday season in full swing, the surge in online shopping brings not only increased sales but also heightened security risks for ecommerce platforms.Managing an ecommerce API during this time can be quite the challenge. I know how it feels – the time is tight, the team is stretched thin, and the budget is already allocated. Spotting a large-scale attack amidst this chaos? It seems almost impossible.But don't worry, I've got you covered with some quick and easy tips!In this blog, I'm going to show you how to test for some of the most common API vulnerabilities in ecommerce systems. You'll also get a glimpse into how attackers exploit these weaknesses. And you might be surprised at just how straightforward it can be to identify and fix these issues!So, let's dive in and get your API security up to speed for this busy holiday season.
Setting Up Your Testing Environment
To effectively follow along with our security testing guide, you'll need to set up the OWASP Juice Shop, an intentionally vulnerable web application designed for training and security testing purposes. We recommend using the Docker version for a streamlined setup process. You can find the necessary resources and installation guide here.In addition to the OWASP Juice Shop, you'll require a tool capable of capturing and editing requests from a web application. For this purpose, we'll be utilizing the Burp Suite Community Edition, which is a free version of the popular Burp Suite. This tool is ideal for intercepting and modifying HTTP requests and responses, making it a valuable asset for identifying and exploring API vulnerabilities.Alternatively, if Burp Suite doesn't suit your needs, other excellent options include ZAP (Zed Attack Proxy), MITM (Man in the Middle) proxy, or Postman. Each of these tools offers unique features and capabilities, and like Burp Suite, they are available either for free or as open-source software. This flexibility ensures that you can choose the tool that best fits your specific testing requirements and preferences.
Exploring the OWASP Juice Shop for Practical Demonstration
For our demonstration, we'll be using the OWASP Juice Shop, an intentionally vulnerable web application that simulates a real-world ecommerce site. This platform, designed for security training, mimics an online juice store. It features a JavaScript front end and a RESTful API back end, offering a realistic environment for testing.When you first access the OWASP Juice Shop, you'll notice it operates like any typical online store. It displays various juices with their prices. As a user, you can create an account, add items to your cart, update your payment details, and proceed to checkout. This familiar functionality allows you to experience and test real-world ecommerce operations.However, the Juice Shop includes additional complexities to enhance the testing experience. Certain products have purchase limits, restricting how many items a single user can buy. This introduces a layer of business logic that is common in ecommerce platforms. Additionally, there's a wallet top-up feature, enabling users to add virtual currency to their accounts. These elements not only make the testing environment more realistic but also provide various scenarios to explore different types of vulnerabilities and security challenges.
Identifying Common Business Logic Errors: Quantity and Price Manipulation
A prevalent issue in ecommerce systems is the manipulation of quantities and prices, a type of business logic error. To understand how this works, let's consider a practical scenario. Imagine you're adding an expensive item to your cart, priced at $50. The vulnerability we're exploring allows us to then add a negative quantity of another item – for instance, -4 units of an item priced at $10 each.This manipulation effectively creates a discount of $40 on the cart. As a result, the original $50 item's cost is reduced to just $10. This kind of vulnerability exploits the logic used by the system to calculate total prices and can lead to significant financial losses for the ecommerce platform. It's a simple yet powerful example of how attackers can use business logic flaws to their advantage, underscoring the importance of thorough security testing in ecommerce APIs.
Getting Started with Burp Suite: Identifying the API
First up, let's fire up Burp Suite and dive into the world of APIs.This step is crucial because, while the vulnerability we're discussing isn't exclusive to APIs, it's more commonly found in them. APIs often rely on the assumption that the user interface has already validated input data, which might not always be the case.So, how do we know we're dealing with an API here? A couple of telltale signs give it away. For starters, our application references a /rest/ endpoint collection. REST, standing for Representational State Transfer, is a popular style in API design. It's not just about the technicalities; it's also a bit of a style statement in the modern API world.Another clue is the use of JSON (JavaScript Object Notation) in requests and responses. Despite its name, JSON isn't just for JavaScript. It's a universal language understood by APIs far and wide, with plenty of libraries available for serialization and deserialization in various programming languages.So, with Burp Suite up and running, we're all set to confirm that we're indeed interacting with an API and ready to explore further!
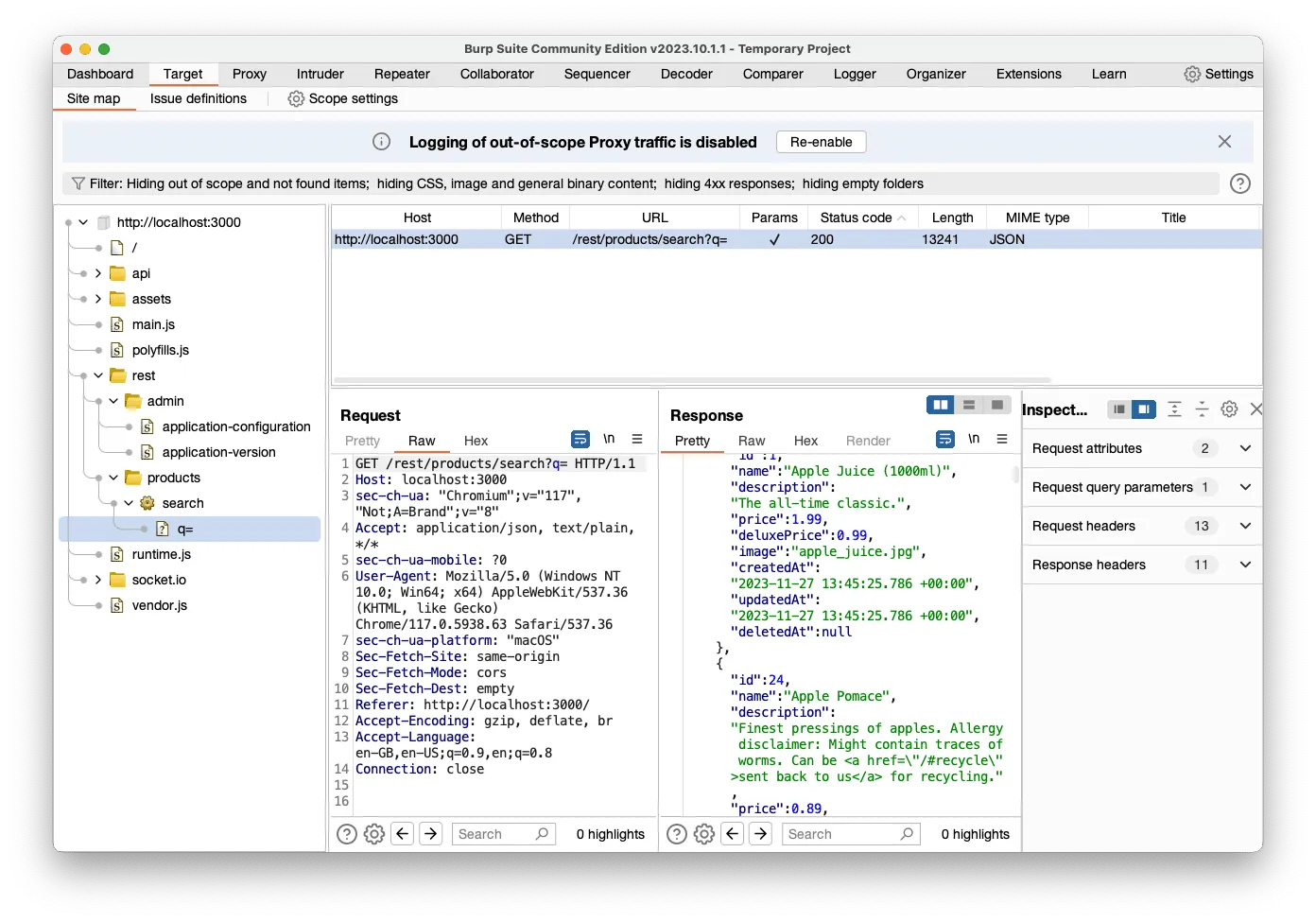
Time for Some Shopping Cart Magic!
Alright, it's time to have some fun with our shopping cart. We're going to add a bunch of banana juice – think 11 bottles, each at a sweet price of $1.99. But here's where we get a bit cheeky: we'll also sneak in -10 apple juices, priced the same. Our sneaky goal? To magically tweak our cart total to just $1.99 for all those bananas. It's like pulling a rabbit out of a hat, but with juices!Now, keep in mind, depending on the ecommerce system's logic, we might end up with those 10 apple juices being packed and shipped. Sometimes, the system might just skip over that minus sign, thinking it's a regular order. But hey, we're here to learn about discounts, not to stock up on apple juice (though that wouldn't be too bad, right?).Next up, let's get techy with Burp Suite's Proxy -> Intercept tool. This nifty tool is usually off, but once we switch it on, it's like having a superpower to pause and tweak requests before they hit the server. We're going to use it to play around with the quantities we just added. With the zippy internet and 5G speeds these days, a single click can send a bunch of requests. So, we'll be hitting "Forward" on each request until we spot the one with our juice quantities. Think of it like sorting through a deck of cards until you find the ace!Remember, we can also drop requests, which is like saying, "Nope, you're not going to the server today!" It's all part of the fun in exploring how ecommerce systems handle our cart shenanigans.

Modifying and Forwarding the Request
Upon identifying a request that indicates the quantity of an item, we'll proceed to modify this value. This step is straightforward: simply change the quantity, for instance from 2 to -10. After making this adjustment, we'll forward the request to the server.

Once the modified request has been sent, we can deactivate the intercept function in Burp Suite, as it's not needed for the immediate next steps.
Verifying the Outcome in the User Interface
After modifying and forwarding the request, the next step is to check if our changes have taken effect. Instead of delving into the technical details of the server's response, a more straightforward approach is to simply view the basket through the user interface. This allows us to quickly see if our manipulation was successful.Upon inspection, if the total in the basket shows as $1.99, it indicates that our attempt to use the negative quantity of apple juice as a discount has worked. This change in the total cost confirms the successful manipulation of item quantities in the cart.
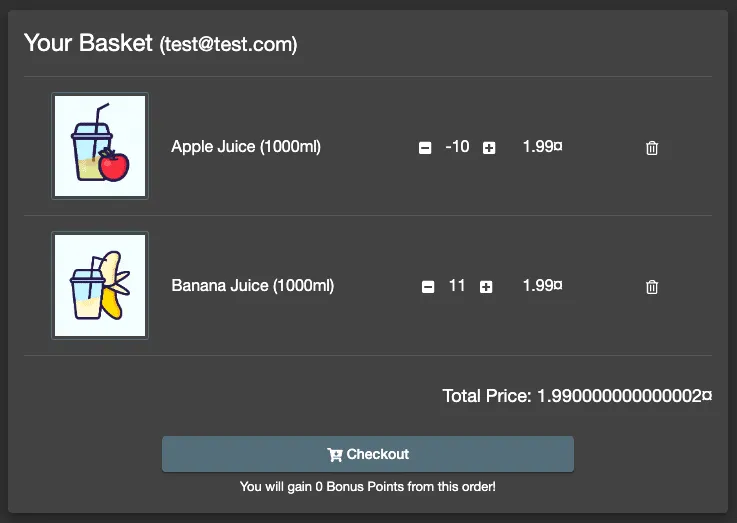
Completing the Checkout Process for Full Confirmation
After observing the successful cart manipulation, the next step is to proceed through the entire payment flow. This is crucial, especially when payment processing is handled by a third-party system. These external systems may have additional checks in place that could identify and flag the discrepancy or even return an error.Therefore, it's important to complete the checkout process to fully confirm whether the manipulation goes undetected through all stages of the transaction. However, it's not necessary to wait for the actual delivery of the products, particularly if you're testing in a non-live environment. This final step in the checkout process helps in understanding how different components of the ecommerce system interact and respond to the manipulated data.
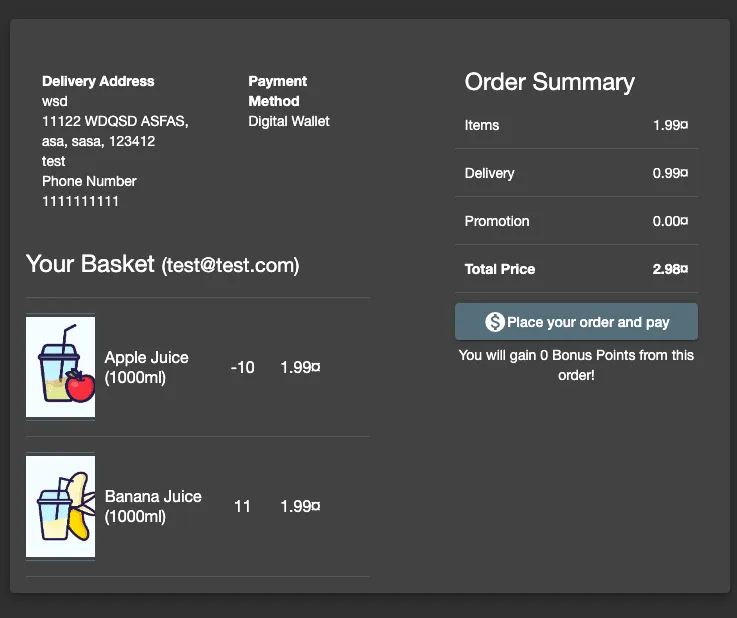
Success and Insights: The Impact of a Simple Vulnerability
And just like that, we've managed to get 11 Banana Juices for the price of one, plus delivery! This demonstrates a simple yet impactful vulnerability, which can be particularly tricky to detect during the hectic holiday season. Such business logic issues might stay hidden for years, potentially costing a company thousands.While identifying this vulnerability seems straightforward, the reality is more complex, especially with large APIs where new endpoints are added daily. This is where Traceable’s comprehensive API security platform comes into play. It gives security teams a complete view of their API landscape, aiding in everything from threat detection to managing the attack surface.Curious to see how Traceable can bolster your API security? Feel free to arrange a demo and discover more.
About Traceable
Traceable is the industry’s leading API Security company helping organizations achieve API visibility and attack protection in a cloud-first, API-driven world. Traceable is the only intelligent and context-aware solution that powers complete API security – API discovery and posture management, API security testing, attack detection and threat hunting, and attack protection anywhere your APIs live. Traceable enables organizations to minimize risk and maximize the value that APIs bring their customers. To learn more about how API security can help your business, book a demo with a security expert.
The Inside Trace
Subscribe for expert insights on application security.
.avif)



