Intelligent Rate Limiting for API Abuse Prevention


Intelligent Rate Limiting for API Abuse Prevention
Introduction Malicious API attacks have increased 137% in 2022 alone, and despite the security measures in place, they are predicted to become the primary attack vector in 2023. We have already seen that to be true with data breaches seen at T-Mobile and an ethical hacker’s disclosure of vulnerabilities he was able to exposed at Toyota. It is evident that InfoSec teams need to tighten API protection to boost the overall security posture. API throttling and rate-limiting are two important concepts for managing APIs that need dedicated focus.
The Increasing Need for Intelligent Rate Limiting
As API traffic volumes increase manifold businesses have to look at multiple means to impose rate limits on their APIs. The need for doing that stems from:
- Not overwhelming the systems - The goal of any API backend is to provide a high-quality service for all client requests. If a single client floods the server with requests that basic need cannot be met. The sudden or sustained spikes in API traffic will impact that API and all downstream services which that API is front ending in most cloud native environments.
- Breach Service SLAs - APIs must be able to handle specific amounts of traffic to meet the needs the clients which rely on these APIs have to sustain their business needs. To do this, typically system owners control their client's rates, so they stay within expected bounds for service-level agreements (SLA) which they have agreed with their clients.
- Operating expenses and cloud costs - Most APIs are hosted in the cloud these days and they can consume large amounts of resources all the way from computer to network to storage costs. This is also true when APIs have dependencies on 3rd party APIs which are charged based on consumptions like Salesforce, Twilio or Plaid APIs.
Identify the Right APIs and Attributes for Rate Limiting
“Interesting” APIs - APIs which are critical to the business function and can severely impact continuity when overwhelmed need to be identified upfront. In few cases, the business is aware of such APIs and their capacity - this is the easy but rare scenario. In majority of the cases, businesses struggle to capture the “interest” metric in their APIs. That’s where Traceable can help by using the security analytics functionality by providing all the API endpoint traffic and merging that with information of sensitive data, authentication, source of the traffic (BOTs, Residential proxy, TOR, Anonymous VPN’s etc).
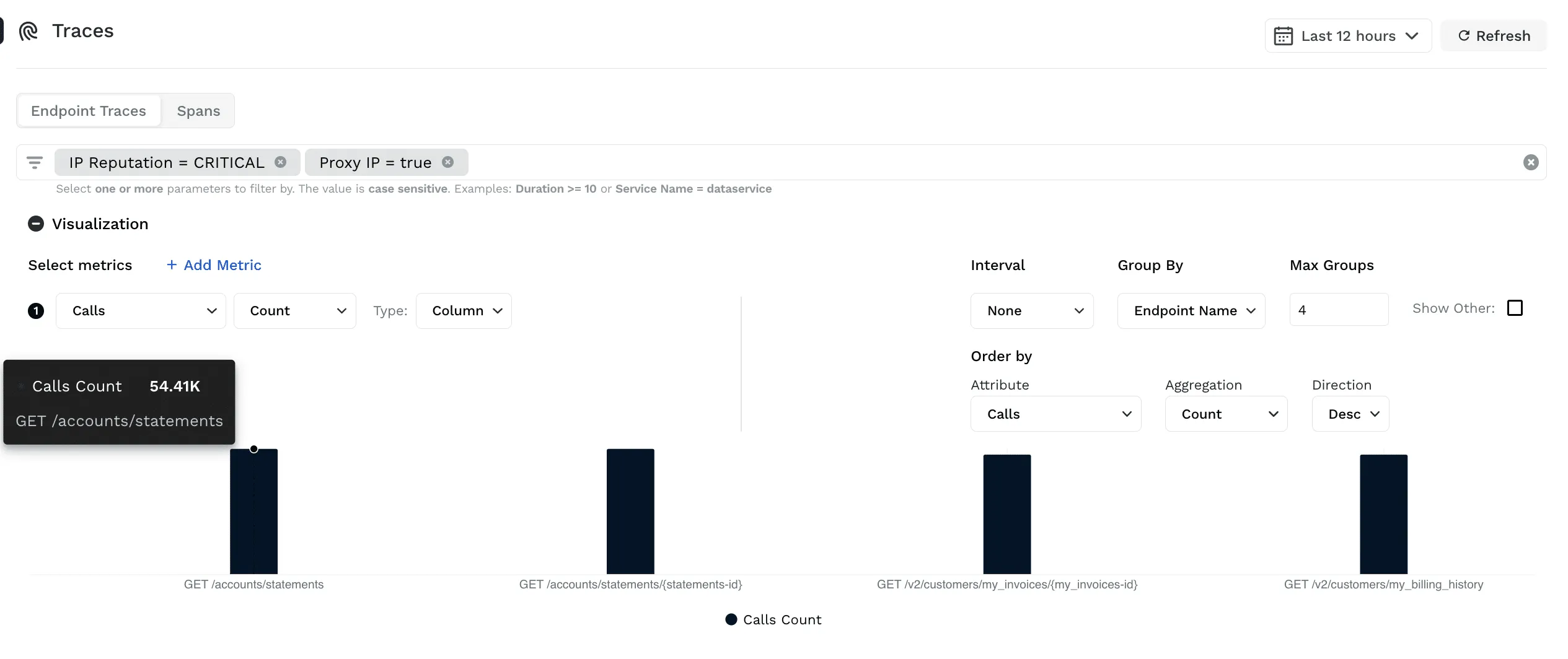
“Suspicious” Users - Sometimes a group of users target a few endpoints with some malicious intent. Identifying and stopping them is very crucial in the smooth functioning of the business. Traceable helps in identifying such users or user groups as well as their intended target APIs and sensitive data (PCI, PII, HIPAA, GDPR etc) or materially significant data they access (payment info, referral amounts, gift card numbers, etc) that are specific to the business.


Apply Policies for Rate Limiting
Traceable allows security teams to apply policies to rate limit APIs and/or users by defining known candidates or broader options in their absence, defining crucial conditions to identify the targets where rate limiting is essential for the business applications to function smoothly.Along the same lines, Traceable allows options to define rate limits manually or with GraphQL APIs which is useful when the intended volume of the endpoints is known. Traceable also provides options to dynamically calculate the rates based on usual traffic and use that to rate-limit endpoints and/or users.Businesses can apply these policies to detect overuse of endpoints or to even block such abusing users from accessing the application.


Along the same lines, Traceable allows options to define rate limits manually or with GraphQL APIs which is useful when the intended volume of the endpoints is known. Traceable also provides options to dynamically calculate the rates based on usual traffic and use that to rate-limit endpoints and/or users.
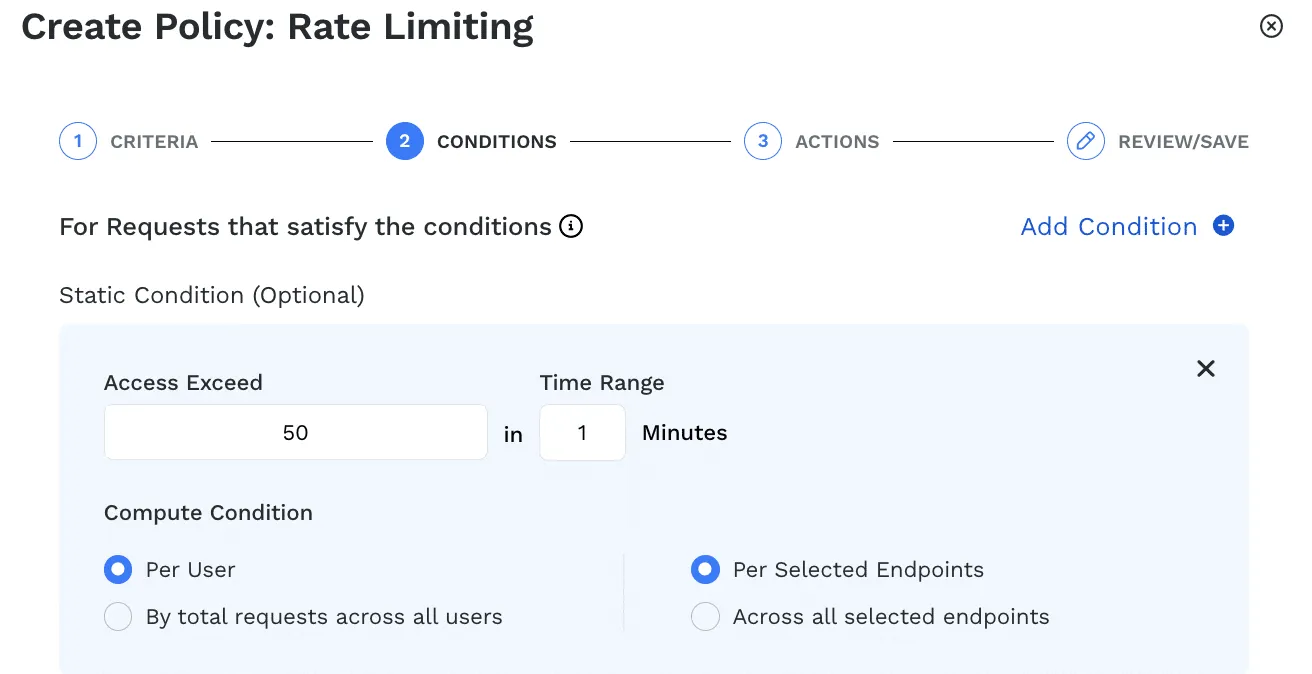
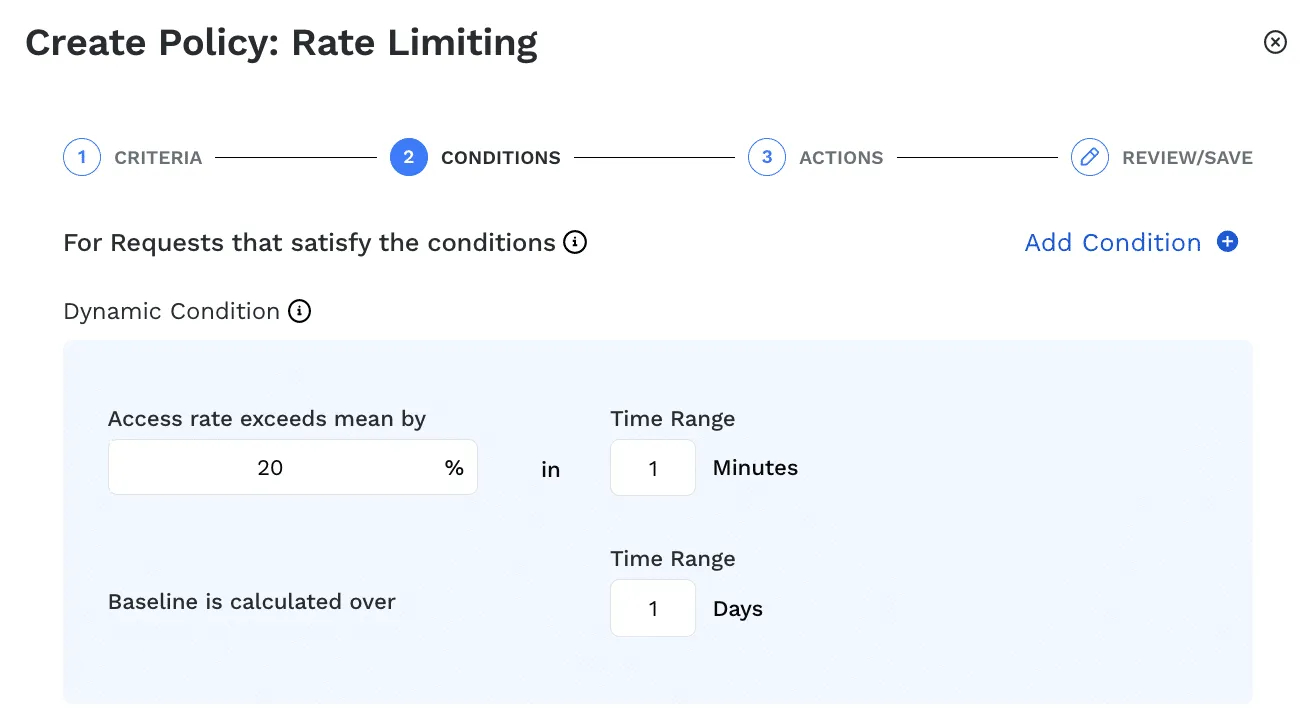
Organizations can apply these policies to detect overuse of endpoints or to even block such abusing users from accessing the application.
The Bottom Line
Attackers have been specifically targeting mobile and Web applications to hijack API calls and to use automated attacks on critical business APIs. They target APIs to take over accounts, steal tokens, scrape business-critical data, and perform application distributed denial of service (DDoS) attacks. API Rate limiting using contextual information on normal API access rates per source type is the best way to understand when your APIs have been targeted to take the necessary remedial action. At Traceable we started with the data lake approach for all APIs (external and internal) and all users (malicious, suspicious, benign) to protect you from these sophisticated attacks. To learn more about Traceable's Intelligent Rate Limiting, download the solutions brief on Zero Trust API Access.

About Traceable
Traceable is the industry’s leading API Security company that helps organizations achieve API protection in a cloud-first, API-driven world. With an API Data Lake at the core of the platform, Traceable is the only intelligent and context-aware solution that powers complete API security – security posture management, threat protection and threat management across the entire Software Development Lifecycle – enabling organizations to minimize risk and maximize the value that APIs bring to their customers. To learn more about how API security can help your business, book a demo with a security expert.
.avif)



