Lessons from IBM's 2022 Cost of a Data Breach Report


IBM Released their 2022 Cost of a Data Breach Report: Here are the Key Takeaways
IBM just released the 2022 Cost of a Data Breach Report, and new disturbing information was presented, in terms of how the cyber threat landscape has evolved in just one year. First, the actual cost of a data breach has risen significantly, especially for highly regulated industries such as financial services and healthcare. And secondly, the United States continues to suffer the highest cost of data breaches – coming in at $9.44 million.This year, IBM added analysis of several new cost factors: extended detection and response, risk quantification, MFA, and zero trust point-solutions. Each of these costs resulted in a lower than average data breach cost. Additionally, the report examined cloud vulnerability and the impact of remote work on organizations.The study concludes that minimizing high costs of data breaches requires a holistic approach to cybersecurity. Many of us in the security industry know this and continue to contend with this challenge every day. However, it’s important to reiterate – consolidation is a must, and strategic investments in solutions that give organizations better visibility and the capability to simplify their environment is hugely needed. Specifically, the report recommends security tools that share data between systems in a central dashboard, and investments in security orchestration, automation and response (SOAR), Security Information and Event Management (SIEM), managed detection and response software, and XDR to improve detection and response times while integrating with your existing solutions and achieving lower overall costs and data breach lifecycles.Adopt Unified Endpoint Management (UEM), endpoint detection and response (EDR) and Identity Access Management (IAM) to mitigate risks associated with remote work by allowing deeper insight and oversight that speed investigations and response time associated with remote work.As organizations continue to include remote work and hybrid multi-cloud environments, adoption of zero trust security models helps prevent data breaches by protecting data, limiting accessibility, and requiring context.
Key Takeaways:
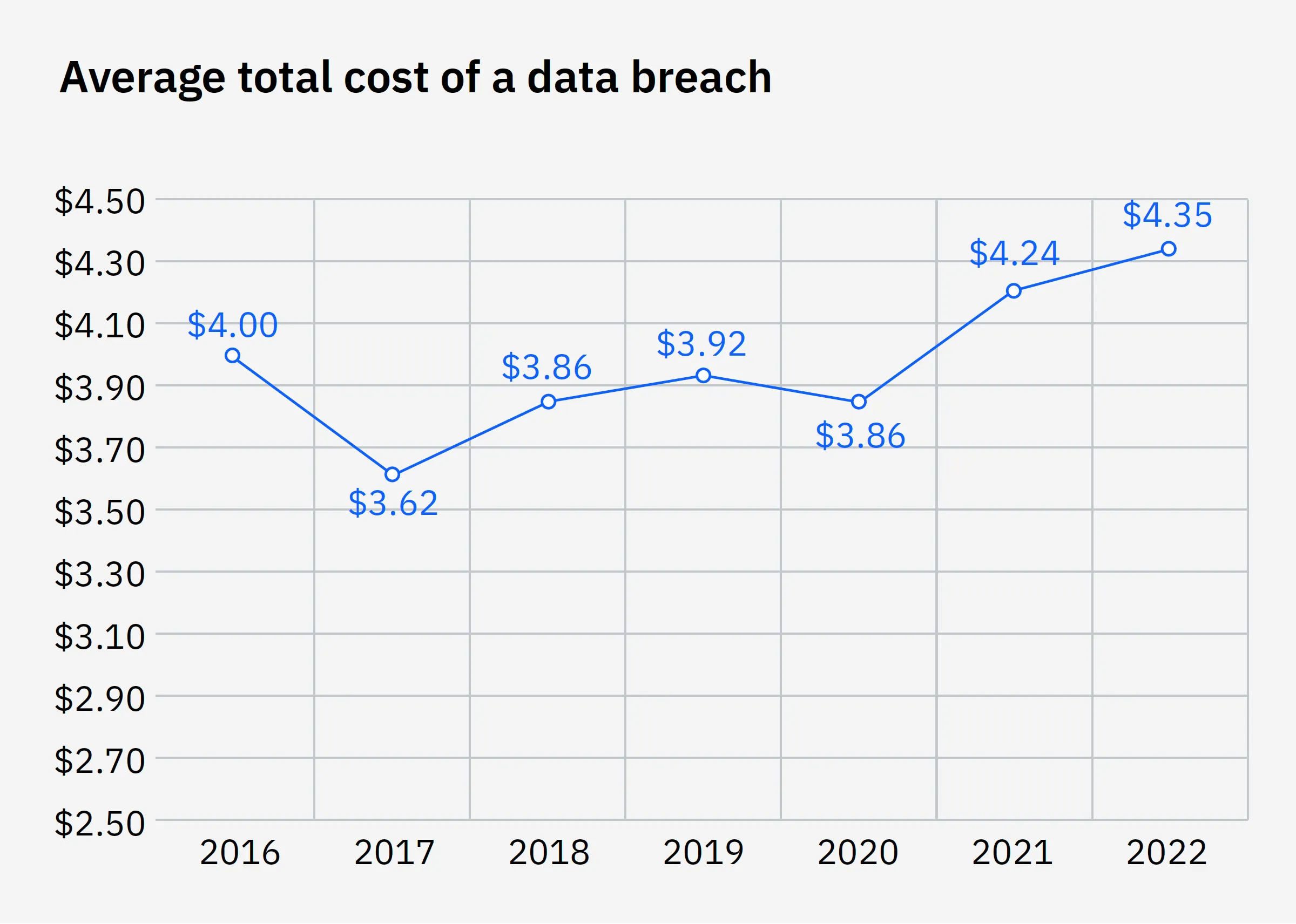
- The average cost of a data breach was USD 4.35 million, an all-time high
- For the first time in six years, detection and escalation costs became the largest share of data breach costs of four categories (detection and escalation, lost business, notification, and post breach response).
- Stolen or compromised credentials is still the most common cause of a data breach, representing 19% of breaches. These breaches have the longest breach lifecycle at 327 days. 2 other common causes for data breaches are cloud misconfiguration at 15% and third-party software vulnerability at 13%.
- Organizations with a high level of compliance failures had an average breach cost of USD 5.57 million.
- 59% of companies do not deploy a zero trust architecture, and among critical infrastructure organizations, a whopping 71% do not deploy zero trust architecture. These organizations incur an average cost of USD 1 million over the standard average.
- The highest cost of any country has been maintained for the past 12 years by the United States at USD 9.44 million.
- When remote working was a factor in causing the breach, costs of a breach were roughly USD 1 million greater than those breaches which did not factor remote working, which requires more integrations, connections, and APIs.
Cloud Remains a Primary Point of Data Breaches for Organizations
Cloud data breaches become more likely when cloud-native applications and microservice architectures are used, due to the abundance of APIs. Lack of visibility into API sprawl has led to an API crisis - 91% of organizations experienced an API security incident in 2020, according to Security Magazine, Feb 2021.
- Of organizations in their early stages, 43% have not started applying security practices to protect their cloud. Of those in their mid-stage, 34% were applying cloud security, and 23% of mature stage organizations applied security practices regularly. 17% of organizations have not begun applying cloud security practices.
- 45% of breaches occurred in the cloud, with hybrid cloud breaches costing an average of USD 3.8 million, private cloud costing USD 4.24 million, and public cloud costing USD 5.02 million. Organizations using hybrid clouds had a shorter breach lifecycle than those using public or private clouds.
Appropriate Security Solutions Positively Impact Data Breach Lifecycle and Costs
Intelligent solutions like security automation are needed to address false positives and to accelerate incident response in an industry suffering from time constraints and human error. API Security solutions play a role in accelerating security initiatives and automation.
- Deploying security AI and automation saved an average of USD 3.05 million. The 65.2% difference of an average breach cost represents the largest cost savings in the study. Companies deploying full security AI and automation additionally experience a 74-day shorter average time to identify and contain the breach. Use of security AI and automation jumped roughly one-fifth from 2020 to 2022.
- Three factors associated with the lowest costs for data breaches, compared to the average, were AI platforms, a DevSecOps approach, and the use of an Incident Response team.
- Risk Quantification significantly minimizes data breach costs, of the 47% (less than half) of the companies that employed Risk Quantification, companies saved an average of up to USD 2.10 million.
- Shorter data breach lifecycles were associated with lower overall costs. For example, a breach lifecycle of less than 200 days was associated with an average cost of USD 3.74 million. Data breaches longer than 200 days averaged USD 4.86 million. This is a 26.5% difference.
- Roughly 75% of organizations studied indicating having an IR plan, and of those, 63% regularly tested the IR plan. Significant breach cost savings, roughly USD 2.66 on average, are associated with having an IR team and regularly testing.
- Mature stage organizations identified and contained data breaches much faster that early stage organizations, with a breach lifecycle of 237 days for mature organizations, their life cycle is 40 days shorter than the global average and 64 days shorter than the average for early stage organizations. Early stage organizations had an extensive breach lifecycle, with an average of 345 days, and mid-stage organizations had a breach lifecycle consistent with the global average time to contain a breach of 277 days.
Highly Regulated Industries Suffer the Costliest Data Breaches
Because of the high value data, highly regulated industries are heavily targeted and maintain the highest cost in data breaches. Healthcare and Fintech are hit the hardest, and therefore can reduce lifecycle costs by using security automation solutions such as API security.
- Highly regulated industries maintain the highest in cost in data breaches. The most expensive for 12 consecutive years, Healthcare breach costs hit a record high this year, costing an additional USD 1 million to cost USD 10.10 million overall, and up by 41.6% since 2020. Financial organizations are next highest, roughly USD 5.97 million, pharmaceuticals follow, averaging USD 5.01 million, technology technology at USD 4.97 million and energy at USD 4.72 million.
- In high data protection regulatory environments such as healthcare, financial, pharmaceutical, and education, data breach costs tended to accrue costs in years following the breach. An average of 24% of data breach costs accrued more than 2 years after the initial breach, most likely due to regulatory and legal costs associated.
The Bottom Line
The lack of Security Automation tools in the tech stack of so many companies illustrates a primary flaw in how security is being addressed by companies today. Saliently addressing various security concerns - IBM identifies cloud as being a primary point of weakness. However, it’s imperative that you invest in security solutions that include API security that can further secure your sensitive data. Given that the vast majority of sensitive data is now transmitted via API, this is non-negotiable.
About Traceable
Traceable is the industry’s leading API security platform that identifies APIs, evaluates API risk posture, stops API attacks, and provides deep analytics for threat hunting and forensic research. With visual depictions of API paths at the core of its technology, its platform applies the power of distributed tracing and machine learning models for API security across the entire software development lifecycle. Book a demo today.
The Inside Trace
Subscribe for expert insights on application security.
.avif)



