Traceable API Security Platform Updates - July 2023


Traceable API Security Platform Updates - July 2023
The Traceable AI team has been busy adding new capabilities and enhancing existing ones to better meet your API Security needs. Here is a sampling of some of the additions in July 2023.
Service filter added to application flow map
If you have a lot of services and find it hard to find the one you are looking for in the application flow map, this new service filter will help.The new dropdown shows the top 15 services by volume (for performance reasons) and the search box lets you search through all the services to quickly find the one you are looking for. Once selected the flow map will show from the perspective of that service(s).Here's a short video of it in action[video width="1830" height="1078" mp4="https://traceable.ai/wp-content/uploads/2023/02/filter-app-flow-map.mp4"][/video]
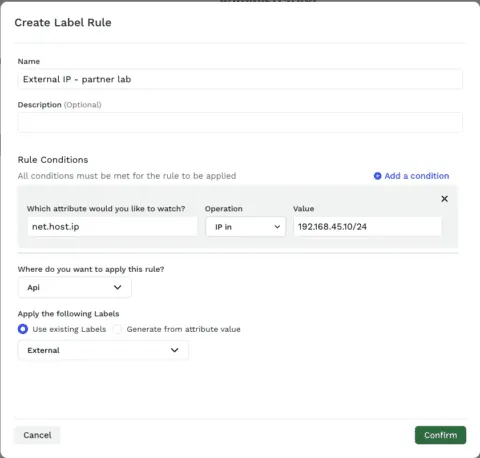
Two new IP-based operations for label rules
We’ve heard that many of you want to automatically label your API endpoints based on what network block a request or response comes from. To support this we've added 2 new operators for labels - “IP in” and “IP not in”. They take one or more (comma-separated) network blocks using CIDR notation.
Here's a short video of it in action
[video width="1806" height="1014" mp4="https://traceable.ai/wp-content/uploads/2023/02/label-rule-ip-operations.mp4"][/video]
Add rules to mark APIs as internal/external
In some environments automatic classification of APIs as external/internal needs to be overridden because:
- Original IP addresses are not sent
- APIs being accessed from external IP addresses are still considered internal because those are specific IP addresses used by sister companies such as Venmo accessing PayPal's APIs.
Previously, correcting these classifications had to be done one by one using the UI. We’ve added a rules-based automation that can be used to override the default internal/external classifications. These rules can be based on a wide range of criteria in the API call including the two new label criteria “IP in” and “IP not in”.The count on the top of the API endpoints page will also be updated to reflect any changes.
Tune Risk Scoring using custom labels
Sometimes you want to customize risk scoring based on your organization's specific requirements, such as different risk scores for different environments (production vs dev), or different risk profiles for business-critical APIs.You can now influence the global risk-scoring rules by using any labels. Previously this ability was limited to using one of the 4 existing labels - critical, sentry, etc. You can now use any labels that you have previously created to align with your existing workflows.Note: "Internal" and "External" labels are not allowed to prevent double counting since internal/external is already factored in the "API Access" category for calculating risk scores.Here's a short video of it in action[video width="1806" height="1014" mp4="https://traceable.ai/wp-content/uploads/2023/02/risk-score-custom-labels.mp4"][/video]
Easily identify when an API endpoint was last scanned
Many customers want to spot-check that their vulnerability scanning coverage is as expected. At several large financial customers, their Auditors want this functionality to verify that all APIs are being scanned and then look at the evidence.You can now use the API Endpoints view to find out when a particular endpoint was last scanned, and then easily navigate to that specific scan in API Security Testing. This is done by adding 2 optional columns to the API Endpoints table - Scan ID & Scan Timestamp.Here's a short video of it in action[video width="1806" height="1014" mp4="https://traceable.ai/wp-content/uploads/2023/02/AST-from-endpoints.mp4"][/video]
Confidence/impact-based threat activity prioritization
We are constantly working to improve the algorithms by which we filter the noise and bring you only the important threat activity that needs your attention. Adding confidence and impact-based assessments is part of that refinement. In this first phase of the confidence/impact-based threat activity prioritization:
- Every event is tagged with impact based on parameters such as - response codes, Sensitive data in response, and error/empty responses.
- Every event is tagged with confidence based on criteria like - API/params learning, # of rule hits, IP reputation, proxy/BOT/TOR, etc
- Filters are available on the threat activity summary and detailed screen.
This is another step on the journey to threat prioritization, easier user workflows, and false positive tuning. The next step is a three-tuple-based grouping which will yield the benefits of reducing the total number of detections and better impact scoring.Here's a short video of it in action[video width="1806" height="1014" mp4="https://traceable.ai/wp-content/uploads/2023/02/confidence-impact-threat-activity-level.mp4"][/video]
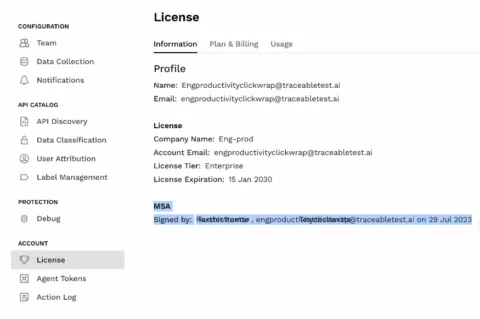
Master Subscription Agreement signing flow for new customers
Now when a new customer account owner logs in for the first time, they will be presented with the request to sign the MSA agreement. This will not be presented to existing customers. The details that it is signed, by who, and when will also be reflected in the License preferences screen.
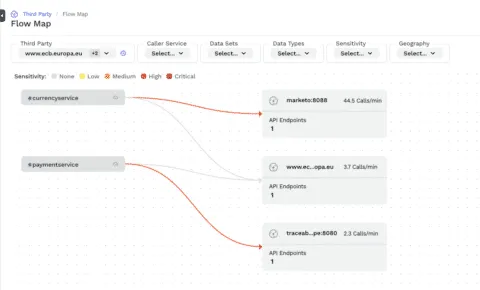
Apigee agent support for third-party APIs
Provides you visibility into your 3rd party API use and the data they are sending, if you use Apigee gateway either as a pass-through or to route all outgoing 3rd party calls through.Apigee agent 1.27.0 now captures exit calls to the back-end from Apigee to support 3rd-party API capture. This requires Traceable Platform agent 1.32.1 or later.

About Traceable
Traceable is the industry’s leading API Security company that helps organizations achieve API protection in a cloud-first, API-driven world. With an API Data Lake at the core of the platform, Traceable is the only intelligent and context-aware solution that powers complete API security – security posture management, threat protection and threat management across the entire Software Development Lifecycle – enabling organizations to minimize risk and maximize the value that APIs bring to their customers. To learn more about how API security can help your business, book a demo with a security expert.
The Inside Trace
Subscribe for expert insights on application security.
.avif)


