Traceable API Security Platform Updates - June & July 2024


This past month’s releases include major improvements to data classification, UX improvements for API catalog, AST changes, and a new threat activity UI for improved visibility and more efficient analysis.
Granular Data Classification Settings
Data classification lays the foundation for Traceable’s data flow mapping and sensitive data detection capabilities. We have released several changes to our data classification capabilities that improve the granularity of severity and suppression policies and data classification rules:
- Sensitivity and suppression configurations can now be modified per datatype. Prior to this update, sensitivity and suppression policies were applied at the dataset level.
- Data classification rules for each datatype can now be scoped to specific URLs.
- Data classification rules for each datatype can now be targeted to only leaf nodes in a nested JSON payload.
You can access these new features by navigating to Settings > Data Classification > Datatypes and creating a new datatype or editing an existing datatype. Read more in our docs.
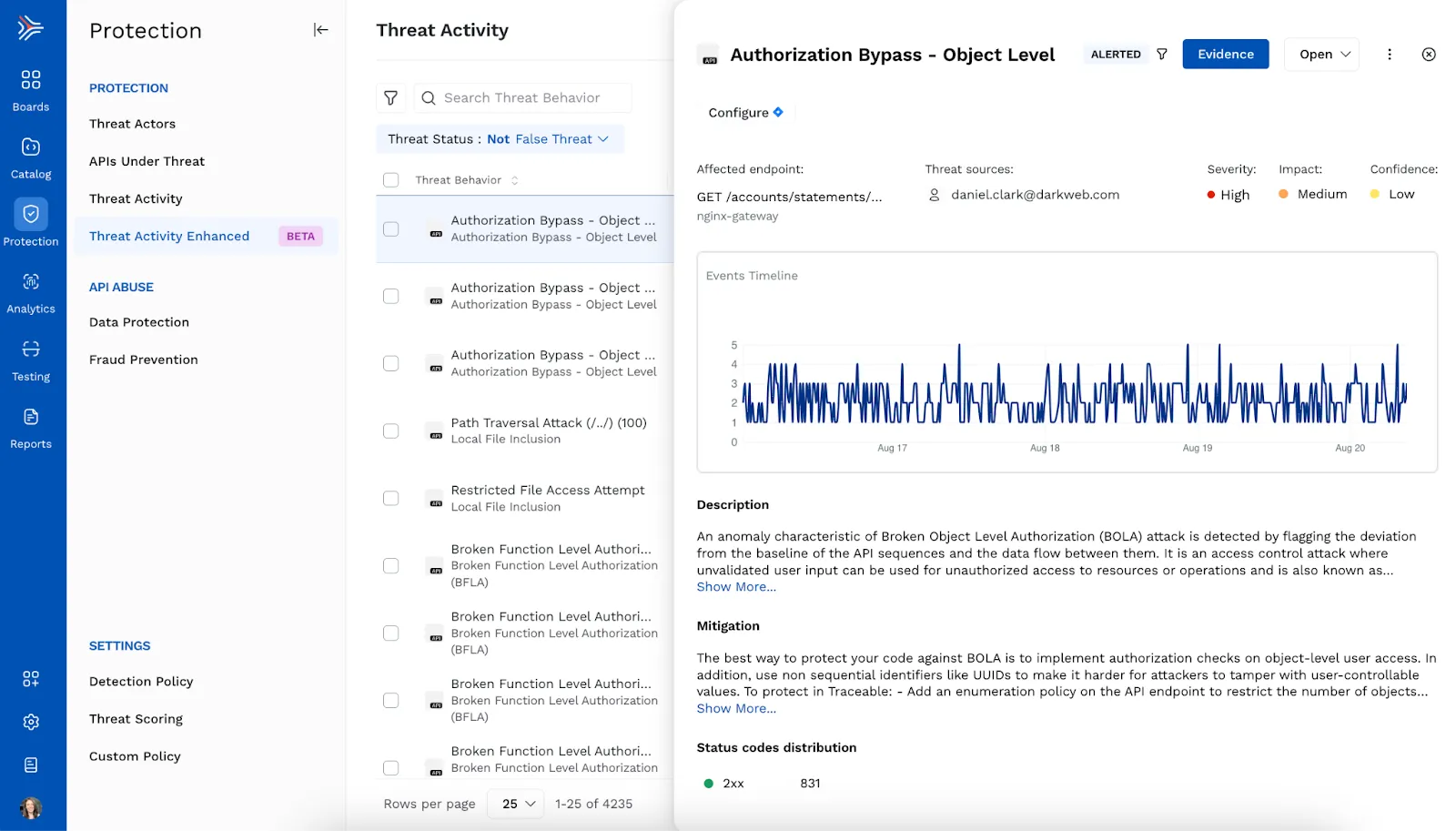
New Threat Activity UI Available in Beta
As a security analyst or incident responder, the ability to quickly and effectively triage alerts is paramount. The less time you spend on false positives, and the sooner you can identify a true positive, the more quickly you can shut down an active threat. We are excited to release a new Threat Activity UI in beta. We’ve redesigned the threat activity experience with a focus on enabling customers to triage threat activities more efficiently, and focus on the ones that have the highest impact on APIs from a potential breach perspective. Traceable customers can experience the new UI today by navigating to Protection > Threat Activity V2 (Beta).
The new UI includes several key changes:
- Improved Event Groupings: We’ve improved the way we group events into threat activities to reduce the total number of alerts and improve visibility into threats driven by the same actor or occurring on the same API endpoint. In the original version of Threat Activity, events were grouped based on rule type alone. In the new version, events are correlated and grouped by looking at account rule type, actor, threat behavior, and API endpoint over a time period. As repeated threats from the same actor on the same endpoint can be used to detect persistent attacks, this allows analysts to more easily identify related activity and saves time on triage and investigation.
- New Filters: We’ve expanded the set of filters available in Threat Activity to include more activity, threat actor, and endpoint attributes. Using these cascading filters can help analysts more easily prioritize threat activities and hone in on true positives and eliminate false positives. You can also save filters for easy reuse or to share with others on your team.
- Bulk Actions: You can now perform bulk actions on threat activities such as creating an exclusion, initiating a status change, creating a JIRA ticket, or pushing specific activities to a SIEM or a SOAR. For example, if you’ve identified that all threat activities associated with a particular actor are false positives, you can filter to activities associated with that actor, select all, and update the status to “False Threat.”
- Detailed Summary and Evidence Per Threat Activity: For each threat activity identified, we will now display a detailed summary, including a description, mitigation steps, and an event timeline. We also auto populate the time range for each threat activity and clearly identify the anomalous attribute per event.
We are excited for you to try out the new Threat Activity UI and eager to hear your feedback. Please try it out and let us know what you think.
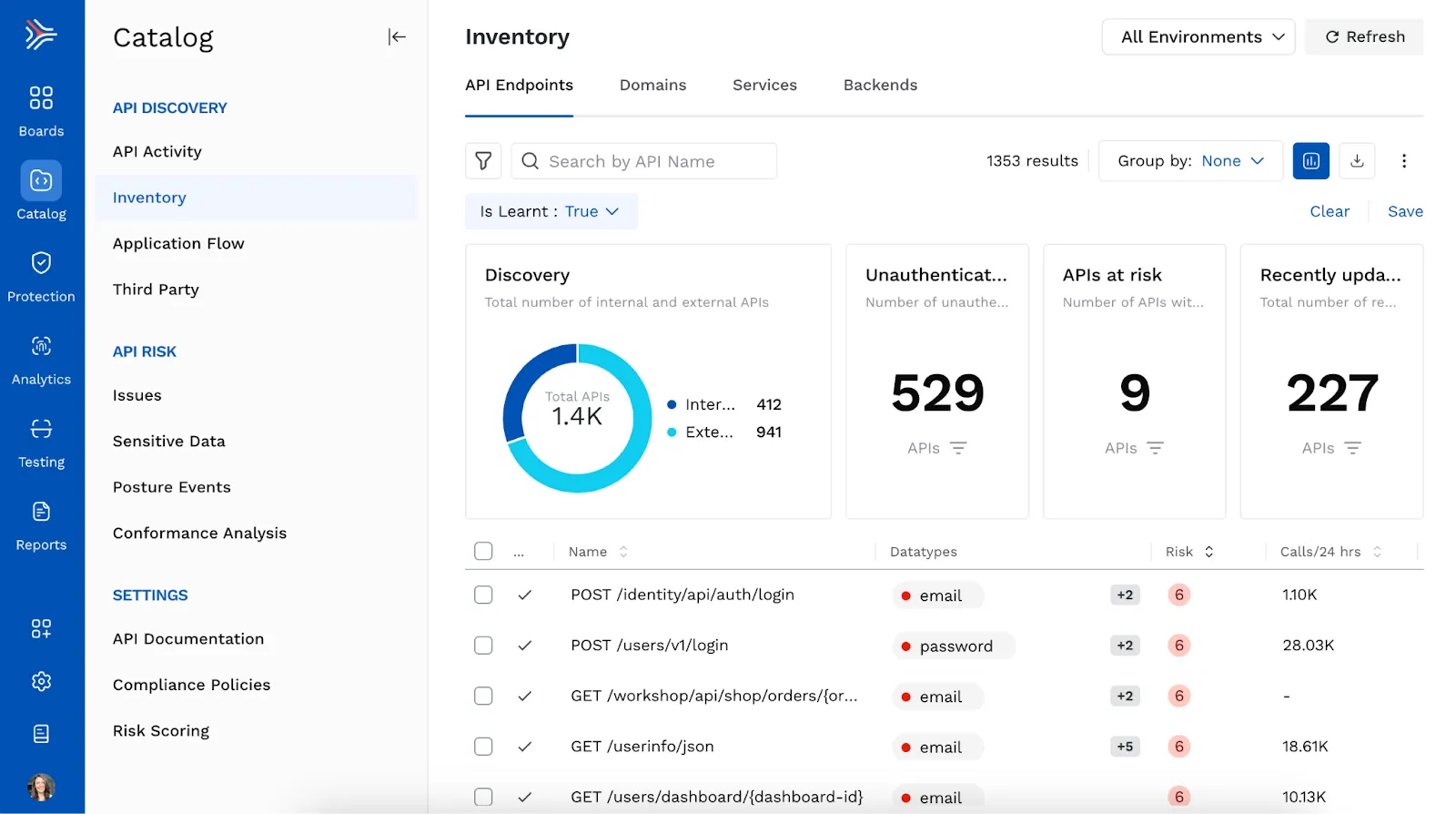
UI Enhancements for API Catalog
We’ve made several usability enhancements to the API Catalog UI, including:
- Reorganized and simplified left navigation menu.
- Updated “Inventory” page with separate tabs for API endpoints, domains, services, and backends.
- Improvements to “Sensitive Data” page for quick insight into sensitive datatypes observed in your API endpoints.
We are staging the rollout of the new UI for existing Traceable customers over the next month.
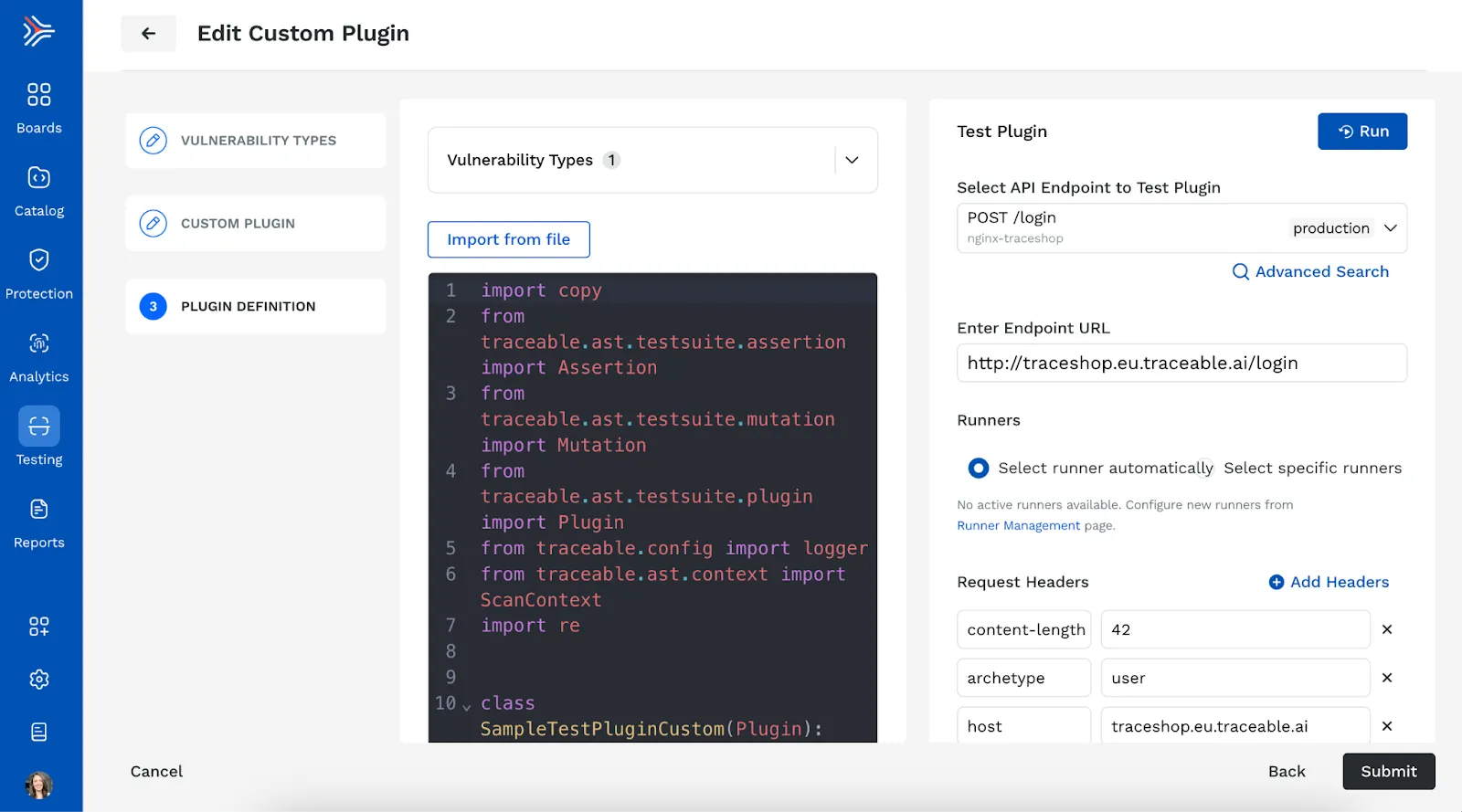
API Security Testing Custom Plugin Tests
Traceable’s API Security Testing allows you to create custom plugins to implement specific security rules or logic tailored to your requirements, such as enforcing particular security policies. We recently released an update to this feature that allows you to test custom plugins on a single API endpoint before saving them, so you can reduce potential configuration errors and utilize custom plugins more confidently. With custom plugin testing, you can compile and preview plugin results, providing an opportunity for review and adjustment before saving the plugin and configuring a scan run.
The Inside Trace
Subscribe for expert insights on application security.
.avif)



