Traceable API Security Platform Updates - October 2023


In October the Traceable team was busy releasing a monster set of great additions and enhancements. From industry-first deep visibility into encrypted gRPC calls, to tracking and getting notifications on almost any important system event, to new ways to search and filter, and even save and share your query results, to optimization of how external control points are used. There is a treat for everyone in October’s releases.Here are some details on these exciting additions that happened in October 2023.
gRPC Now Supported Over Encrypted Traffic
gRPC is gaining in popularity which means it is becoming a more attractive target for API attacks and data exfiltration. Discovering gRPC APIs in your apps is a start, but it’s hard to manage the security posture of your gRPC APIs if you can’t see past the TLS encryption and what data is flowing through them.Traceable now provides this critical visibility by being able to see inside encrypted gRPC API traffic without needing to set up in-line decryption points. This is done using our proven eBPF data collection technology.Here's a short video of it in action:[video width="1920" height="1080" mp4="https://traceable.ai/wp-content/uploads/2023/10/grpc-data-posture.mp4"][/video]
Security Posture Events
To stay on top of your API security posture it’s important to keep track of change events. Doing so maintains an audit trail, provides details of changes, and can notify you when changes of interest happen. For example, knowing when a new API has been discovered, or getting notified when a risk score for a highly used API endpoint increases.In Traceable’s API Catalog, you can now see all the change events that might impact the security posture of an environment:
- New API discovered
- Risk score changed
- New sensitive data type discovered
- New sensitive data type shared with 3rd party API
- New service discovered
- New vulnerability discovered
Every change, including details, is viewable in the UI, and you can also be notified when any of these changes occur (see next item).Here's a short video of it in action:[video width="1920" height="1080" mp4="https://traceable.ai/wp-content/uploads/2023/10/posture-change-tracking.mp4"][/video]
Enhanced Notification Options
Product security and infosec engineers often find it valuable to be notified about specific events happening within their tools. This might be for alerting, or for governance of the tool itself.In addition to notifications on threat activity, Traceable can now also send notifications on security posture events (see previous item), and many other activities such as:
- Threat actor status and severity state changes
- Protection configuration changes such as specific policy changes, exclusions, IP range changes, rate limiting, and many more
- Team activities such as user logins, invites, deletions, and additions
- Data classification configuration changes such as editing a data type
- Data collection activity
- Notification configuration changes such as creating a new notification rule or channel
These notifications can be sent to different configured channels, such as email, Slack, S3, Splunk, and custom webhooks to make sure that the updates get to where they are needed.Here's a short video of it in action:[video width="1920" height="1080" mp4="https://traceable.ai/wp-content/uploads/2023/10/notification-options.mp4"][/video]
Threat Activity Impact and Confidence Scoring
Security analysts and engineers in the SOC need to quickly prioritize their attention on the threat activities that matter the most. To help them focus on the most important detections, each threat activity in Traceable now has dynamically calculated Impact and Confidence scores.These scores are based on many details about the detected events and activities, such as return codes, API endpoint risk scores, and sensitive data types for the Impact scores; and IP intelligence, anomaly, and abuse velocity details for the Confidence scores.This makes it easy to find the high-priority threats by setting filters to Severity = high/critical, Impact = high, and Confidence = high.Here's a short video of it in action:[video width="1818" height="1080" mp4="https://traceable.ai/wp-content/uploads/2023/11/impactconfidence-scoring.mp4"][/video]
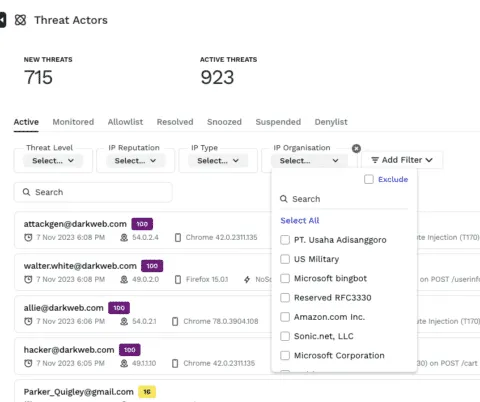
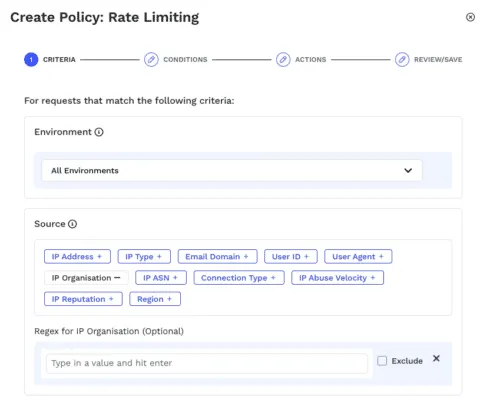
New Uses for IP Organization Source Attribute
Many bot-based attacks, such as credential stuffing, enumeration, ATO, and fraud, come from specific IP Organizations. While figuring out attack remediation strategies, Infosec and SOC engineers can use these details. IP Organization data, along with ASN, geo, and IP types such as bots, proxies, and anonymous VPNs, can be combined to block subsequent attack traffic. The same information can be sent to SIEM and SOAR tools for SOC analysts to use in forensics.Traceable has added the ability to use the IP Organization source attribute in security policies and as a filter for threat activities and threat actors. The IP Organization source attribute is also available when doing Analytics in the Trace Explorer.
Saved Queries in Trace Explorer
As an Infosec or SOC engineer, you can analyze API-based attacks by forming queries to search through threat data along with API requests, responses, threat intel information (IP reputation, abuse velocity, etc), and source of the traffic (BOTs, VPN, Proxies, etc). It's helpful to be able to repeat, iterate, and share your search queries.You can now save and access your most used queries instead of having to re-enter them. This also simplifies sharing and collaboration by referring to the saved queries. The Traceable Customer Success team has also found this useful for relaying findings to customers.Here's a short video of it in action:[video width="1818" height="1080" mp4="https://traceable.ai/wp-content/uploads/2023/11/saved-dl-queries.mp4"][/video]
Download Query Results from Trace Explorer
Trace Explorer query results can be valuable outside of Traceable, either as input to other tools or to share with others. For example, to help the infosec and fraud prevention engineers analyze the data offline.You can now export the trace query results as a CSV file for further analysis and sharing. Depending on the threat you are investigating different data might be interesting to share. You can specify the exact parameters you want to download, such as the threat source (eg. Bot, VPN, IP ASN, etc), or the request/response details.Here's a short video of it in action:[video width="1818" height="1080" mp4="https://traceable.ai/wp-content/uploads/2023/11/exporting-dl-queries.mp4"][/video]
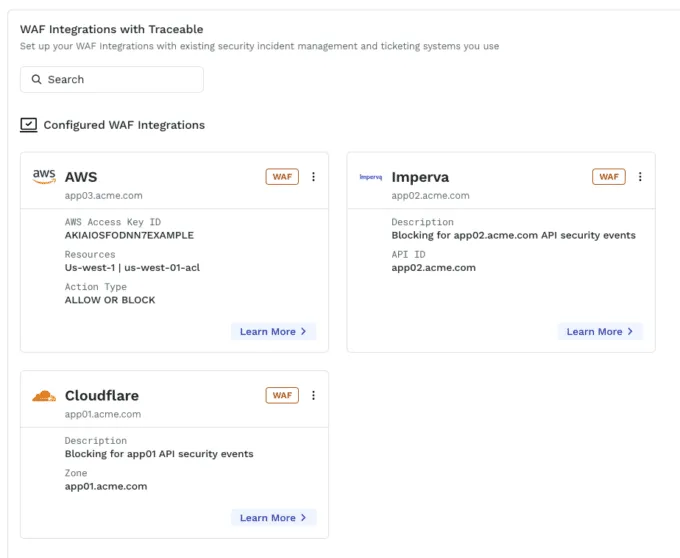
Multi-WAF Integrations
Most large enterprises have multiple WAFs deployed across their environments and need to protect their applications from threat actors across the entire deployment, not just at one point at a time. A holistic approach is far more effective.Traceable has been able to automatically block detected threat actors and malicious IPs at the integrated WAFs without any manual intervention. Now, these blocking options will be automatically pushed to all integrated WAFs at once. This ensures that if certain threat actors have been seen in certain parts of your App/API stack they will also be blocked on other parts protected by other WAFs. This is especially useful in multi-cloud, multi-API Gateway, and multi-WAF deployments for larger enterprises.

About Traceable
Traceable is the industry’s leading API Security company that helps organizations achieve API visibility and attack protection in a cloud-first, API-driven world. Traceable is the only intelligent and context-aware solution that powers complete API security – API discovery and posture management, API security testing, attack detection and protection, anywhere your APIs live. Traceable enables organizations to minimize risk and maximize the value that APIs bring their customers. To learn more about how API security can help your business, book a demo with a security expert.
The Inside Trace
Subscribe for expert insights on application security.
.avif)


