Traceable API Security Platform Updates - September 2023


In September we focused on making API testing even easier for those not using auto-configuration, added new threat analysis primitives to streamline threat hunting and as a bonus for those who want to use table-supported explorations we made the user experience even better.Here are some details on these exciting additions that happened in September 2023.
Simplified Authentication Setup for API Security Testing
Traceable’s API Security Testing in XAST-live mode will automatically configure necessary authentications for your tests using data from live traffic. But for DAST mode, and XAST-replay mode when all data is redacted, authentication will need to be configured. With these enhancements, users can spend less time and effort on setting up these authentication configurations.New configuration user interface - Set up authentication configuration details without writing a single line of script. For authentication types API Key, Basic Auth, Bearer Token, Content Signature, HMAC, JWT, Mutual TLS, OAuth/OAuth 2.0, and PoP Token Signature.Secure Credential Management - Securely store and manage your API authentication credentials within Traceable.Test & debug authentication configurations - Right from the authentication setup screens you can test, debug, and fix your configurations to make sure they are entered correctly without having to run a full API test policy.Here's a short video of these in action:[video width="1920" height="1080" mp4="https://traceable.ai/wp-content/uploads/2023/09/ast-auth-config-test.mp4"][/video]
Filter and Group by IP Subnet in Threat Analytics
When using Traceable to do threat analysis you can now filter to see only transactions from IP addresses that are in a defined subnet, and then you can group by subnet mask when visualizing those results.If you are seeing attack patterns from specific subnets it can accelerate your analysis to see transactions grouped by subnet, as opposed to individual IP addresses. This has immensely helped several customers in multiple threat-hunting scenarios.Here's a short video of it in action:[video width="1920" height="1080" mp4="https://traceable.ai/wp-content/uploads/2023/09/filter-by-subnet.mp4"][/video]
Filter and Group by IP Organization in Threat Analytics
When using Traceable to do threat analysis you can now filter and group by the IP Organization that a transaction’s IP address came from.Filtering and viewing by the IP Organization can help narrow down requests to potentially malicious transactions if they are from an organization with a poor reputation. Combining this information with an IP type, such as “anonymous VPN” or “proxy”, can help provide useful insights.Here's a short video of it in action:[video width="1920" height="1080" mp4="https://traceable.ai/wp-content/uploads/2023/09/filter-by-ip-org.mp4"][/video]
User Page Preferences Saved Across Sessions
Your table column preferences, per page, are now saved across sessions. If you hide a column or edit the column configuration via the UI, those preferences will be stored and will be honored in your subsequent visits to the page. This applies to all pages in the Traceable UI.This user experience enhancement makes using Traceable more efficient while doing such tasks as threat hunting through API transactions in the API Data Lake, looking through API endpoints for ones that need attention, viewing the latest security events of concern, and other table-related tasks.Here's a short video of it in action:[video width="1818" height="1080" mp4="https://traceable.ai/wp-content/uploads/2023/09/save-user-table-prefs.mp4"][/video]
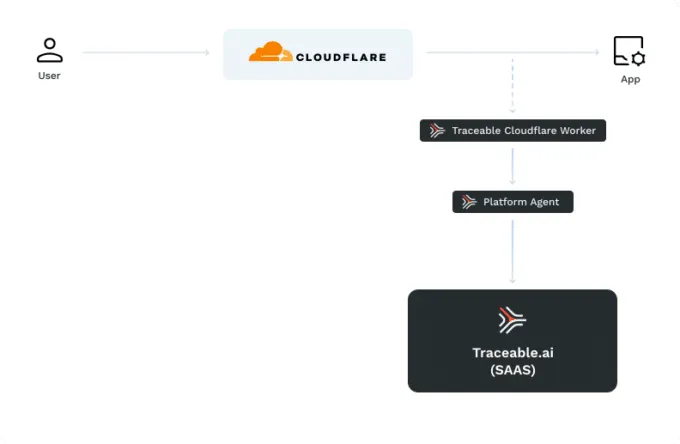
Support for Binary Data in Encoded Bodies in Cloudflare Workers
Cloudflare Workers is a serverless computing platform that enables developers to deploy and execute JavaScript code at the edge of Cloudflare's global network. Traceable integrates with Cloudflare Worker to collect data for API security analysis. Traceable can now collect and analyze binary data that is sent in encoded bodies through Cloudflare Workers.This addition helps ensure that no important data or context clue is missed while identifying and stopping malicious behavior.

About Traceable
Traceable is the industry’s leading API Security company that helps organizations achieve API protection in a cloud-first, API-driven world. With an API Data Lake at the core of the platform, Traceable is the only intelligent and context-aware solution that powers complete API security – security posture management, threat protection and threat management across the entire Software Development Lifecycle – enabling organizations to minimize risk and maximize the value that APIs bring to their customers. To learn more about how API security can help your business, book a demo with a security expert.
The Inside Trace
Subscribe for expert insights on application security.
.avif)


