The Business Case for API Security: Why API Security? Why Now?


The Business Case for API Security:Why API Security? Why Now?
We are just about to finish yet another year -- 2022. And in terms of cybersecurity and specifically, API Security, the past 12 months has been quite a challenge for many industries.As with any emerging or new attack surface, many security teams aren’t always aware that it 1) really exists, 2) if it actually poses a legitimate risk to the organization, and if so, to what extent, and 3) if they are aware of the risk, whether or not current deployments are helping to solve that particular issue for the organization already.However, when it comes to APIs, the challenge isn’t always obvious, and the attack types are more insidious. Most organizations simply do not know their current API inventory, and this is a major problem.
The reality is, there are thousands of APIs in organizations, running on multiple clouds, and they are growing each day.

And considering the complexity of APIs and a phenomenon like API Sprawl, most organizations simply don’t have visibility into how many APIs they have, where those APIs reside, and what those APIs are doing.
In addition, organizations are using outdated, unreliable approaches to secure their environments, such as legacy Web Application Firewalls (WAF) or other solutions for data loss prevention, but none of them are sufficient (nor were designed with the intention of API security) for protecting the API layer. The bottom line is that APIs are now the biggest concern when it comes to abuse, fraud and data loss. These kinds of security incidents have a massive impact on organizations in terms of financial loss, brand value erosion, as well as compliance, given mandates such as FFIEC, and other regulatory guidance on data protection.
According to Gartner...
- By 2024, API abuse and related data breaches will nearly double.
- By 2022, API abuse will move from an infrequent to the most-frequent attack vector, resulting in data breaches for enterprise web applications.
- By 2021, 90% of web-enabled applications will have more surface area for attack in the form of exposed APIs rather than the UI, up from 40% in 2019.
- 88% of boards regard cybersecurity as a business risk rather than solely a technical IT problem.
- APIs are critical to the success of organizations’ digital transformation programs. In a Gartner survey, 70% of enterprises cited APIs as important to digital transformation and API security as their top challenge.
And according to Sapio Research, financial crimes and disruption in partner and customer operations tied for first place as the most common consequences of cyber attacks on companies in the United States in 2022.
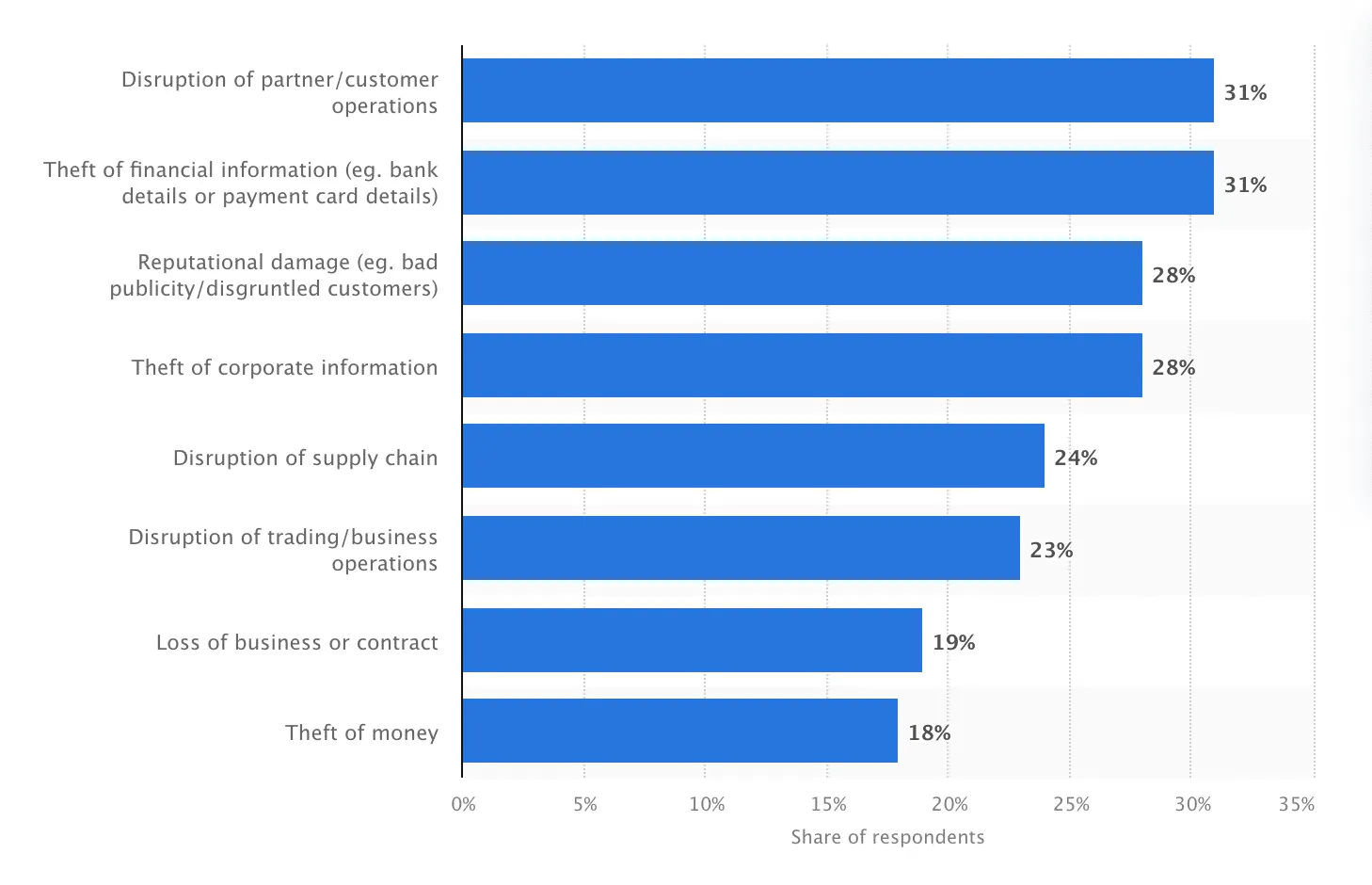
API Abuse and API Fraud are Becoming the Top Attack Vectors
API abuse and API fraud have also recently become front and center for organizations across multiple industries. Some of the largest, recent data breaches happened because APIs were being abused in some way. The Australian wireless service provider, Optus, recently suffered a data breach, where the attacker used an unauthenticated API endpoint to gain access to customers’ sensitive data. This was the first time a major telecommunications company in Australia suffered from such a large and public breach, bringing a huge spotlight to the problem of APIs for the country, and for the world at large. With more information being released about the Optus breach, it is becoming clear that companies need to take API security seriously, as the financial costs and damage to reputation consequences are exponentially greater than funding security programs that operate transparently to keep customers and their data secure and private.
More on the Optus Breach from Traceable's CSO, Richard Bird...
While the initial findings suggest that the exposure of tens of thousands of Australians' personal and private data was accidental, neither government agencies nor customers are very forgiving about an accident being used as a rationalization for a security stewardship failure when it comes to critical information about those customers and citizens.
Security solutions need to account for, expose and mitigate human error on the technical side of the equation, because it is clear that regulators and the market will offer little to no forgiveness for these types of breach events.
The real problem with the Optus breach is the egregious "piling on" that is going on in both the corporate world and the solution providers' space. Optus is in the throes of addressing a challenging catastrophic issue, while the media, government agencies and technologists are actively shaming them.
- Richard Bird
Traceable built API Threat Protection capabilities specifically to combat these attack types, along with the prevention of sensitive data exfiltration, account takeover and mitigating other malicious sources such as malicious bots. Download the datasheet here.
Traditional Solutions Such as WAFs and Data Loss Prevention (DLP) Can’t See the API Layer
One of the biggest reasons that APIs are difficult to protect is because API malicious traffic looks normal to security tools like a web application firewall (WAF). In the cases of Venmo and Coinbase, those particular API attacks are perfect examples of this phenomenon. For Venmo, one of their public endpoint unsecured APIs allowed a student to scrape 200 million users’ financial transactions. This looked like normal traffic to their security solution. At Coinbase, an improper API validation allowed an attacker to make unlimited cryptocurrency trades between different currency accounts. Again, this looked like perfectly normal traffic to their security solutions. Another example happened at Shopify. A company insider was able to leverage order APIs to obtain millions of customer records. Data security strategies have traditionally included legacy solutions such as data loss prevention (DLP) platforms and other data exfiltration tools that prevent structured and unstructured data from leaving the organization via the network or email, or cloud collaboration tools. These platforms may also include CASB and, most recently, SASE solutions. While these are effective at stopping data loss at particular points throughout the organization, and are certainly necessary, they weren’t built for visibility into and security of more stealth points of egress, such as APIs. And with the massive growth in APIs, the challenge isn’t going away anytime soon.What we’ve observed, here at Traceable, is that the vast majority of organizations do not know or understand just how much sensitive data is being transmitted through their APIs, and are in desperate need of a solution that can detect and stop data exfiltration events happening via API.
Discover More About the Business Case for API Security
Download the whitepaper to learn even more latest trends and industry insights to help inform your teams about the business case for API Security.

About TraceableTraceable is the industry’s leading API security platform that identifies APIs, evaluates API risk posture, stops API attacks, and provides deep analytics for threat hunting and forensic research. With visual depictions of API paths at the core of its technology, its platform applies the power of distributed tracing and machine learning models for API security across the entire software development lifecycle. Book a demo today.
The Inside Trace
Subscribe for expert insights on application security.
.avif)




