Traceable API Security Platform Updates - November 2023


In November we focused on making the use and sharing of analytics queries easier and more powerful, providing more details for each detected threat to help with more timely fixes, increasing our blocking capabilities with WAF integrations and third-party transactions, and adding to our out-of-band data collection flexibility.Here are some details on these exciting additions that happened in November 2023.
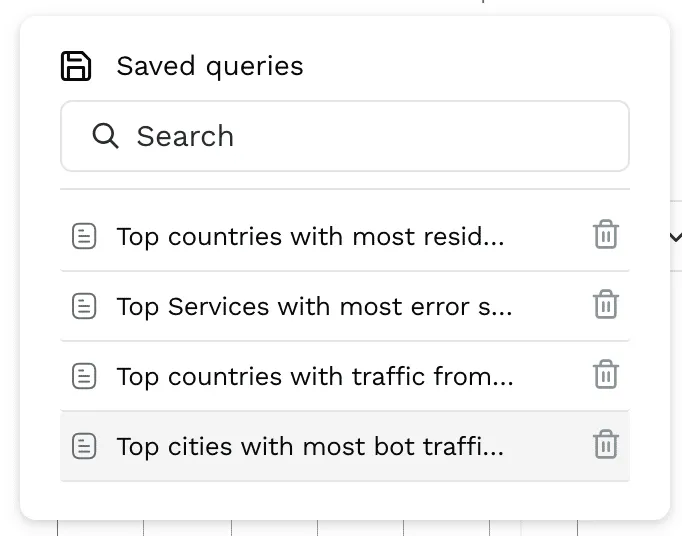
Out-of-the-Box Analytics Queries
As Infosec and SOC engineers analyze API-based attacks they need to go through threat data along with API requests, responses, threat intel information (IP Reputation, Abuse velocity), and the source of the traffic (Bots, VPN, Proxies, etc). The easier they can look across all this data and get an understanding of suspicious behavior, the faster they can identify issues that need attention.Traceable now includes the following queries out of the box:
- Top APIs seeing bot traffic with poor IP reputation, from a data center
- Top countries with the most residential proxy traffic, of poor reputation
- Top Services with the most error status codes, from corporate locations
- Top countries with traffic from a hosting provider, connected from a data center, with high abuse velocity
- Top cities with the most bot traffic, with high abuse velocity to POST APIs, with OK Status codes
Easy customizations of these queries can get you quickly to findings of business logic abuse and behavioral threats. For example, detecting these criteria on unauthenticated APIs, finding sensitive data accessed within the resulting traffic, or identifying traffic spikes associated with that data access.

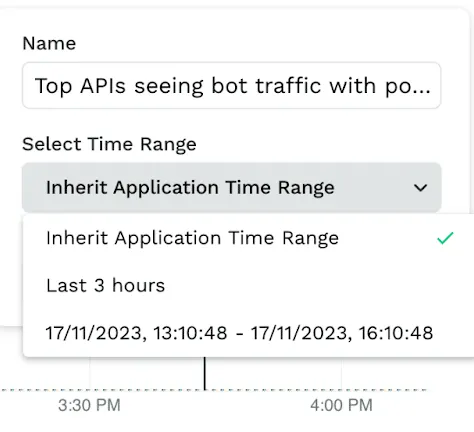
Time Range Flexibility for Saved Queries
For Infosec and SOC Engineers working on attack analysis and threat hunting, saving and sharing queries and findings with others is a key way to collaborate. Including the time range of findings is an important part of the context that usually needs to be shared.Traceable users now have the flexibility to include the time range as part of their saved query. They can choose the time range to be the default page time, a custom time range, or a relative time (eg. last 1 week, last 1 day). This allows Infosec and SOC engineers to share specific queries identifying the time when suspicious behavior or attacks were seen for threat hunting and forensics. They can also share it with their colleagues who can make subsequent updates to allow for better collaboration between threat-hunting efforts.
Threat Activity Description, Mitigation, and Impact Details
Product Security and Development Engineers who need to remediate or mitigate identified threat activity can be more efficient if relevant threat information is more easily available to them. Better information leads to better understanding and faster fixes.Traceable’s Threat Activity dashboard now shows additional details about each threat, including a description, mitigation suggestions, potential impact, and references to further details.This additional information makes detected threats actionable for the Product Security and Development teams. AST Tests can be built to ensure that fixes have addressed the identified vulnerabilities associated with the threat activities.



Custom Signature-Based Blocking for AWS WAF
Product Security and Infosec Engineers, using Traceable with AWS WAFs as a control point, sometimes need the ability to block specific API requests for attacks detected by Traceable. In addition to actor-based blocking, which maps to IP-based blocking in AWS, Traceable now also supports custom signature-based blocking in AWS WAF. Traceable automatically manages the lifecycle of rule creation, updates, and deletions so that Security administrators do not need to take care of individual updates.
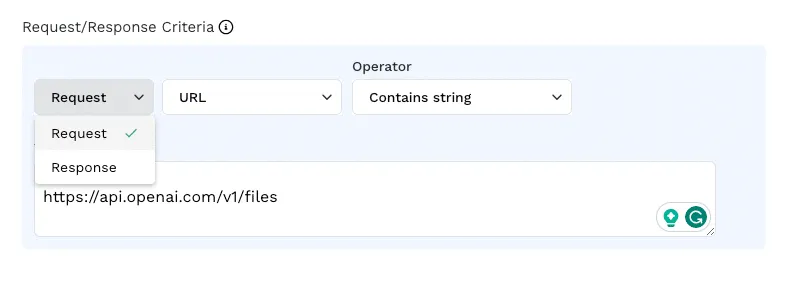
Request-based (Outbound) Sensitive Data Blocking with All Language Agents
Security Administrators and Infosec Engineers might be concerned about API use sending sensitive data out to organizations that are not trusted or against policy. They need the ability to block API traffic based on whether there is sensitive data in the request body. This is needed to protect data in use cases such as Open AI APIs.All of Traceable’s language agents (python, Java, Nginx, Node.js, and GO) now support request-based (outbound) sensitive data blocking. This means that customers can now block any sensitive data being sent in API requests to organizations such as Open AI or other such entities that are not trusted.
New Data Collection Options at the Edge
In addition to all the load balancers, proxies, and gateways that Traceable already supports, Traceable has added support for the following:
- Akana API Management platform
- Axway API Gateway
- Boomi API Gateway
- Citrix ADC (Netscaler)
- GCP Load Balancer (separate from already supported Apigee Gateway)
- Traefik API Gateway
These are all out-of-band data collection methods (asynchronous) so there is no additional latency for the API calls being collected.

About Traceable
Traceable is the industry’s leading API Security company that helps organizations achieve API visibility and attack protection in a cloud-first, API-driven world. Traceable is the only intelligent and context-aware solution that powers complete API security – API discovery and posture management, API security testing, attack detection, and protection, anywhere your APIs live. Traceable enables organizations to minimize risk and maximize the value that APIs bring their customers. To learn more about how API security can help your business, book a demo with a security expert.
The Inside Trace
Subscribe for expert insights on application security.
.avif)


