Who Owns API Security? Introducing the Key Players


In the world of modern application development, APIs (Application Programming Interfaces) are essential for enabling connectivity and functionality to your customers, employees, and partners. However, as the usage of APIs grows, so do the security risks associated with them. Ensuring the security of APIs is not the responsibility of a single individual or team. Instead, it requires the collaboration of multiple stakeholders across various functions.If you are looking to develop your API security program, getting key stakeholders to invest in an API security project is key. Creating a programmatic API security approach that goes beyond basic API discovery requires a broad set of tacticians and visionary team members. To help you understand how to approach building an API security program, here’s a breakdown of the strategic leaders and tactical contributors involved in ensuring comprehensive API security.
Owning the Strategy of API Security
In any organization, securing APIs is a challenge that requires strategic oversight and coordination. The ownership of the process of building an API security program often falls to executive leaders who have the vision and authority to drive these initiatives. In conjunction with application security team members, these leaders play a crucial role in setting the strategic direction, ensuring resource allocation, and coordinating between various groups to implement robust API security measures. The key API security project leaders typically include the Chief Information Security Officer (CISO), the Head of Enterprise Architecture, and the Head of Product & Application Security. Each of these roles brings unique strengths and perspectives to the table, making them indispensable in the quest for comprehensive API security.
- CISO (Chief Information Security Officer) The CISO often takes the lead in API security efforts due to their overarching responsibility for the enterprise's information security strategy. They play a critical role in setting the vision and strategy for API security, developing and enforcing security policies, managing risks, allocating necessary resources, and communicating the status of API security to executive leadership. The CISO's involvement can vary based on the organization's size, with more direct involvement in smaller organizations and less in larger enterprises.
- Head of Enterprise Architecture In larger organizations, the Head of Enterprise Architecture may initiate API security projects. Sometimes reporting through the CTO organization, they are responsible for the organization's overall API management strategy, which includes security as a key component. Their role involves developing and enforcing architectural standards for secure API design, evaluating and selecting appropriate security tools, and ensuring a unified approach to API management, security, and governance.
- Head of Product & Application Security Often, the Head of Product & Application Security is directly responsible for operationalizing API security. Reporting to the CISO, they oversee the security posture of the company's digital products and applications. Their responsibilities include promoting secure design and development practices, managing the security posture of products, overseeing security testing, and handling vulnerability management.
Each of these potential project owners has a different frame of reference in which they view API security. For an organization to achieve high level API security success, these leaders must work together seamlessly. The CISO provides strategic direction and resources, the Head of Enterprise Architecture integrates security within the current technology framework, and the Head of Product & Application Security operationalizes these strategies in the products and applications the business offers their customers. Their collaboration ensures that API security is comprehensive, proactive, and aligned with the organization's overall security goals.
Success Requires Consistent Security Execution
Ensuring the security of APIs goes beyond strategic oversight and planning; it requires hands-on implementation and continuous management. This is where the responsible stakeholders come into play. These teams and individuals are directly involved in the day-to-day tasks of securing APIs, from development through deployment and beyond. Their roles are crucial in identifying vulnerabilities, monitoring for threats, and responding to incidents in real time. By taking proactive measures and maintaining a vigilant stance, these stakeholders help protect the organization's digital infrastructure against evolving security threats. Generally speaking, there are two separate groups with day to day responsibilities for task level action of an API security program.Product & Application Security Product and application security teams are essential for ensuring the proactive security posture of applications throughout their lifecycle. They are responsible for assessing APIs for vulnerabilities before and after deployment and continuously monitoring and managing API security in production. This team plays a crucial role in preventing improperly designed and implemented APIs from being exploited. Product and application security team members understand how applications are built and secured from the ground up providing both infrastructure and development security experience to the team such as:
- Vulnerability Testing and Remediation Experience: These team members are adept at conducting thorough vulnerability assessments and testing. They use a variety of tools and techniques to identify potential security weaknesses in APIs and applications preferably before they can be exploited.
- Subject Matter Expertise in Remediating API and Application Code Issues: Security professionals bring in-depth knowledge and expertise to address and remediate code vulnerabilities. Their experience allows them to quickly identify and fix security flaws, ensuring that applications remain secure.
- Understanding Common API and Application Threat Scenarios: By being familiar with common adversarial threats, product and application security team members help development teams prioritize resources effectively. They guide developers on the most critical security issues to address, ensuring that the most significant risks are mitigated first.
Security Operations (SOC) & Incident Response Security operations and incident response teams focus on detecting, investigating, and responding to threats targeting APIs in production. With API threats on the rise, their ability to identify and respond to API-related threat activity is critical for preventing data breaches and financial losses. These team members are the operational day to day security life blood of an effective application and API security program. They connect the dots between vulnerabilities, infrastructure, code, and security data. SOC and IR API security team members are focused on:
- Continuous Monitoring and Threat Detection: SOC personnel monitor API traffic in real-time, using advanced tools and techniques to detect any signs of malicious activity or abnormal behavior. This involves setting up and managing alerts to identify potential threats as they emerge.
- Incident Investigation and Analysis: When suspicious activity is detected, SOC and incident response teams conduct detailed investigations to determine the nature and scope of the threat. They analyze logs, API call patterns, and other data sources to understand the attack vectors and potential impact on the organization.
- Response and Mitigation Efforts: Upon confirming a security incident, these teams take immediate action to contain and mitigate the threat. This includes isolating affected systems, applying patches or security fixes, and coordinating with other teams to ensure a comprehensive response. They also document incidents and develop strategies to prevent similar threats in the future.
API Security Requires Support From Others
Ensuring robust API security is not solely the responsibility of API and development focused teams. It requires the support and collaboration of various other security functions within the organization. These adjacent support systems play vital roles in reinforcing the security measures implemented by primary security teams. Their contributions are crucial for meeting regulatory requirements, preventing fraud, protecting sensitive data, and ensuring the secure development of APIs. By working together, these teams help create a comprehensive and resilient API security framework. Common supporting groups include:
- Governance, Risk, and Compliance (GRC): GRC teams ensure compliance with relevant laws, regulations, and internal policies. API security posture can be crucial for meeting certain regulatory requirements. Depending on the specific regulations, GRC teams may perform audits, monitor API-related requirements, or enforce specific API security controls.
- Anti-Fraud Teams: APIs are often targeted for digital fraud. Anti-fraud teams focus on detecting and preventing fraudulent activities, such as account takeovers and fraudulent transactions, by analyzing API activity. Their efforts help mitigate the risk of fraud and protect the organization’s resources.
- Data Protection Officers (DPOs): DPOs are responsible for protecting business data and ensuring compliance with data privacy regulations. Given that APIs often handle sensitive data, DPOs leverage API security tools to enforce data protection policies and prevent unauthorized data exposure.
- API Developers: Development teams are on the front lines of API security. They must adhere to secure development policies and maintain APIs by implementing fixes for vulnerabilities identified during security testing. Their collaboration with security teams is essential for ensuring the secure implementation and maintenance of APIs.
Putting This Blog To Work: A RACI Matrix for API Security Stakeholders
A RACI matrix is a powerful tool used to define and clarify roles and responsibilities within a project or process. RACI stands for Responsible, Accountable, Consulted, and Informed, and the matrix helps ensure that every task or decision is clearly assigned to the appropriate stakeholders. By outlining who is responsible for carrying out tasks, who is accountable for the overall outcome, who needs to be consulted for their input, and who should be kept informed of progress, the RACI matrix promotes clarity and accountability. In the context of API security, using a RACI matrix helps coordinate efforts across various teams and functions, ensuring a comprehensive and cohesive approach to protecting APIs. This matrix helps you understand the distinct roles each stakeholder plays in the API security process, facilitating better collaboration and more effective security management.
API Security RACI Matrix
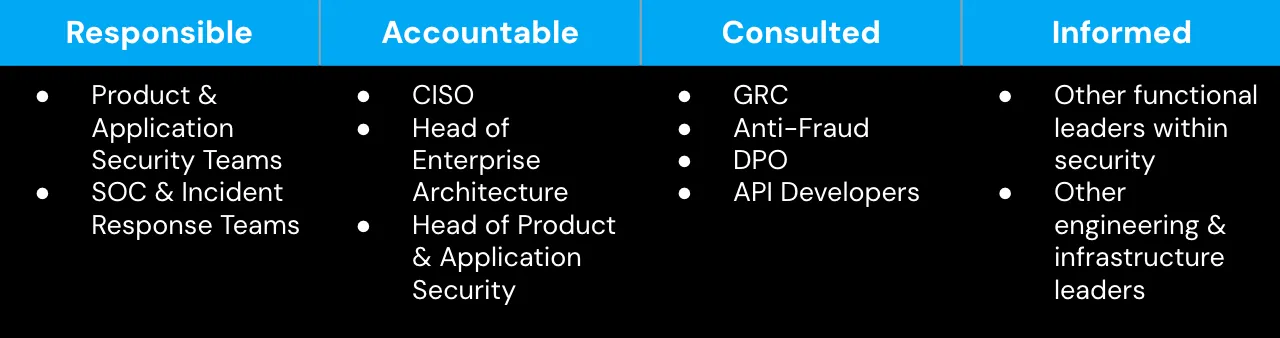
API Security is a Collaborative Effort
Effective API security is a collaborative effort that requires the involvement of multiple stakeholders across various functions. By clearly defining the roles and responsibilities of each key player, organizations can ensure a coordinated and comprehensive approach to API security. This collaborative approach helps safeguard digital assets against evolving threats, ensuring the security and integrity of the organization's applications and data.
About Traceable
Traceable is the industry’s leading API Security company helping organizations achieve API protection in a cloud-first, API-driven world. Traceable is the only contextually-informed solution that powers complete API security – API discovery and posture management, API security testing, attack detection and threat hunting, and attack protection anywhere your APIs live. Traceable enables organizations to minimize risk and maximize the value that APIs bring to their customers. To learn more about how API security can help your business, visit https://www.traceable.ai/.
The Inside Trace
Subscribe for expert insights on application security.
.avif)



